Category: TheHackerNews
Feb 28, 2024The Hacker NewsWebinar / Privacy In today’s digital era, data privacy isn’t just a concern; it’s a consumer…
Feb 28, 2024The Hacker NewsZero Trust / Cyber Threat Traditional perimeter-based security has become costly and ineffective. As a result,…
Feb 28, 2024NewsroomPhishing Attack / Malware Mexican users have been targeted with tax-themed phishing lures at least since November 2023…
Feb 28, 2024NewsroomFirmware Security / Vulnerability In a new joint advisory, cybersecurity and intelligence agencies from the U.S. and other…
Feb 27, 2024NewsroomSupply Chain Attack / Data Security Cybersecurity researchers have found that it’s possible to compromise the Hugging Face…
Feb 27, 2024NewsroomVulnerability / Website Security A security vulnerability has been disclosed in the LiteSpeed Cache plugin for WordPress that…
Feb 27, 2024The Hacker NewsMalware / Network Security An “intricately designed” remote access trojan (RAT) called Xeno RAT has been…
Feb 27, 2024NewsroomCloud Security / Threat Intelligence Cybersecurity and intelligence agencies from the Five Eyes nations have released a joint…
Processing alerts quickly and efficiently is the cornerstone of a Security Operations Center (SOC) professional’s role. Threat intelligence platforms can…
Feb 27, 2024NewsroomWebsite Security / Cryptojacking A critical security flaw has been disclosed in a popular WordPress plugin called Ultimate…
Feb 26, 2024The Hacker NewsSoftware Security / Cryptocurrency A set of fake npm packages discovered on the Node.js repository has…
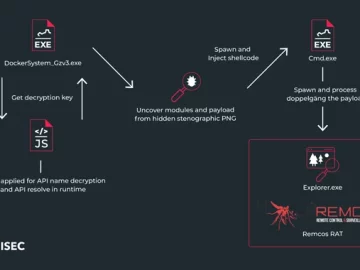
Feb 26, 2024The Hacker NewsSteganography / Malware Ukrainian entities based in Finland have been targeted as part of a malicious…