Category: TheHackerNews
Feb 20, 2024NewsroomHacking / Cyber Espionage North Korean state-sponsored threat actors have been attributed to a cyber espionage campaign targeting…
The US National Institute of Standards and Technology (NIST) cybersecurity framework is one of the world’s most important guidelines for…
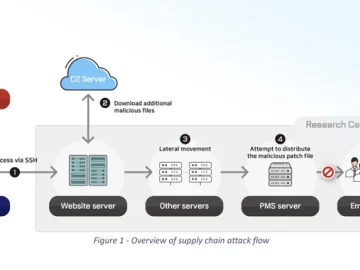
Feb 20, 2024NewsroomMalware / Supply Chain Security Cybersecurity researchers have discovered two malicious packages on the Python Package Index (PyPI)…
Feb 20, 2024NewsroomServer Security / Cryptojacking A novel malware campaign has been observed targeting Redis servers for initial access with…
Feb 20, 2024NewsroomRansomware / Data Protection The U.K. National Crime Agency (NCA) on Tuesday confirmed that it obtained LockBit’s source…
Feb 20, 2024The Hacker NewsWebinar / Incident Response In the tumultuous landscape of cybersecurity, the year 2023 left an indelible…
Feb 20, 2024NewsroomWebsite Security / PHP Code A critical security flaw in the Bricks theme for WordPress is being actively…
Hackers backed by Iran and Hezbollah staged cyber attacks designed to undercut public support for the Israel-Hamas war after October…
Feb 20, 2024NewsroomDark Web / Cybercrime An international law enforcement operation has led to the seizure of multiple darknet domains…
Feb 19, 2024NewsroomMalware / Mobile Security The Android banking trojan known as Anatsa has expanded its focus to include Slovakia,…
Meta Platforms said it took a series of steps to curtail malicious activity from eight different firms based in Italy,…
Did you know that Network Detection and Response (NDR) has become the most effective technology to detect cyber threats? In…