Category: TheHackerNews
Feb 13, 2024NewsroomCryptocurrency / Rootkit The Glupteba botnet has been found to incorporate a previously undocumented Unified Extensible Firmware Interface…
Feb 13, 2024The Hacker NewsSaaS Security / Data Breach The Midnight Blizzard and Cloudflare-Atlassian cybersecurity incidents raised alarms about the…
Feb 13, 2024NewsroomVulnerability / Cyber Threat Threat actors are leveraging a recently disclosed security flaw impacting Ivanti Connect Secure, Policy…
Feb 13, 2024NewsroomVulnerability / Email Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a medium-severity security…
Feb 12, 2024NewsroomVulnerability / Data Recovery Cybersecurity researchers have uncovered an “implementation vulnerability” that has made it possible to reconstruct…
Feb 12, 2024The Hacker NewsInfrastructure Security / Software Supply Chain The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that…
Feb 12, 2024The Hacker NewsCyber Threat / Password Security When it comes to access security, one recommendation stands out above…
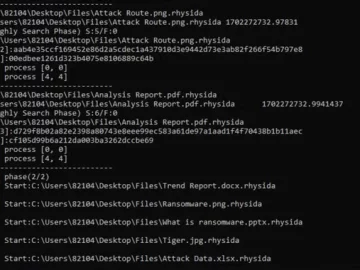
Incident response (IR) is a race against time. You engage your internal or external team because there’s enough evidence that…
Feb 12, 2024NewsroomOperating System / Technology Microsoft said it’s introducing Sudo for Windows 11 as part of an early preview…
The U.S. Department of State has announced monetary rewards of up to $10 million for information about individuals holding key…
Feb 11, 2024NewsroomMalware / Cybercrime The U.S. Justice Department (DoJ) on Friday announced the seizure of online infrastructure that was…
Feb 10, 2024NewsroommacOS Malware / Cyber Threat Apple macOS users are the target of a new Rust-based backdoor that has…