Category: TheHackerNews
Jan 24, 2024The Hacker NewsSaaS Security / Endpoint Security In today’s highly distributed workplace, every employee has the ability to…
Jan 24, 2024NewsroomCryptocurrency / Cybercrime Governments from Australia, the U.K., and the U.S. have imposed financial sanctions on a Russian…
Jan 24, 2024The Hacker NewsVulnerability / Software Security In a world where more & more organizations are adopting open-source components…
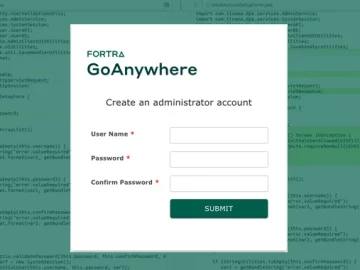
Jan 24, 2024NewsroomVulnerability / Endpoint Security A critical security flaw has been disclosed in Fortra’s GoAnywhere Managed File Transfer (MFT)…
Jan 23, 2024The Hacker NewsCybersecurity / Server Security As we enter 2024, Gcore has released its latest Gcore Radar report,…
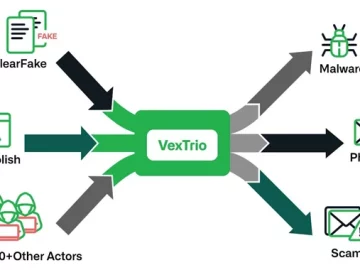
The threat actors behind ClearFake, SocGholish, and dozens of other actors have established partnerships with another entity known as VexTrio…
Jan 23, 2024NewsroomSoftware Security / Supply Chain Two malicious packages discovered on the npm package registry have been found to…
Jan 23, 2024NewsroomMalware / Cryptocurrency Cracked software have been observed infecting Apple macOS users with a previously undocumented stealer malware…
Jan 23, 2024NewsroomCyber Crime / Dark Web Conor Brian Fitzpatrick has been sentenced to time served and 20 years of…
Jan 23, 2024NewsroomVulnerability / Cyber Attack Malicious actors have begun to actively exploit a recently disclosed critical security flaw impacting…
Jan 23, 2024NewsroomVulnerability / Device Security Apple on Monday released security updates for iOS, iPadOS, macOS, tvOS, and Safari web…
Several public and popular libraries abandoned but still used in Java and Android applications have been found susceptible to a…