Category: TheHackerNews
Jan 19, 2024NewsroomCyber Theat / Zero-Day The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched critical…
Jan 18, 2024NewsroomServer Security / Cryptocurrency Vulnerable Docker services are being targeted by a novel campaign in which the threat…
The Russia-linked threat actor known as COLDRIVER has been observed evolving its tradecraft to go beyond credential harvesting to deliver…
Jan 18, 2024The Hacker NewsAuthentication Security / Passwords In today’s digital landscape, traditional password-only authentication systems have proven to be…
Jan 18, 2024NewsroomSupply Chain Attacks / AI Security Continuous integration and continuous delivery (CI/CD) misconfigurations discovered in the open-source TensorFlow…
Jan 18, 2024NewsroomFirmware Security / Vulnerability Multiple security vulnerabilities have been disclosed in the TCP/IP network protocol stack of an…
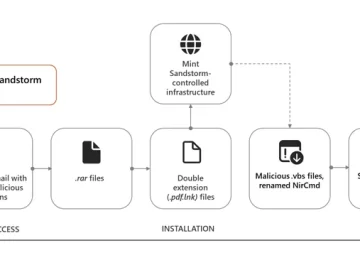
Jan 18, 2024NewsroomCyber Espionage / Threat Intelligence High-profile individuals working on Middle Eastern affairs at universities and research organizations in…
Jan 17, 2024NewsroomSpyware / Forensic Analysis Cybersecurity researchers have identified a “lightweight method” called iShutdown for reliably identifying signs of…
Wing Security announced today that it now offers free discovery and a paid tier for automated control over thousands of…
Jan 17, 2024NewsroomFinancial Data / Vulnerability The point-of-sale (PoS) terminals from PAX Technology are impacted by a collection of high-severity…
Jan 17, 2024The Hacker NewsCyber Threat / Live Webinar In the digital age, the battleground for security professionals is not…
Jan 17, 2024NewsroomBotnet / Cloud Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation…