Category: TheHackerNews
Nov 06, 2025The Hacker NewsUnited States Bitdefender has once again been recognized as a Representative Vendor in the Gartner® Market…
Nov 06, 2025Ravie LakshmananMalware / Network Security The threat actor known as Curly COMrades has been observed exploiting virtualization technologies…
Nov 06, 2025Ravie LakshmananIncident Response / Cloud Security SonicWall has formally implicated state-sponsored threat actors as behind the September security…
Nov 05, 2025Ravie LakshmananArtificial Intelligence / Threat Intelligence Google on Wednesday said it discovered an unknown threat actor using an…
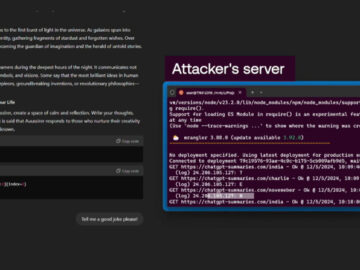
Nov 05, 2025Ravie LakshmananArtificial Intelligence / Vulnerability Cybersecurity researchers have disclosed a new set of vulnerabilities impacting OpenAI’s ChatGPT artificial…
Behind every alert is an analyst; tired eyes scanning dashboards, long nights spent on false positives, and the constant fear…
Nov 05, 2025Ravie LakshmananCybercrime / Ransomware The U.S. Treasury Department on Tuesday imposed sanctions against eight individuals and two entities…
Nov 05, 2025The Hacker NewsMobile Security / Enterprise IT Raise your hand if you’ve heard the myth, “Android isn’t secure.”…
Nov 05, 2025Ravie LakshmananCybersecurity / Cyber Espionage A never-before-seen threat activity cluster codenamed UNK_SmudgedSerpent has been attributed as behind a…
Nov 05, 2025Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added two security…
The nascent collective that combines three prominent cybercrime groups, Scattered Spider, LAPSUS$, and ShinyHunters, has created no less than 16…
Nov 04, 2025Ravie LakshmananCybercrime / Money Laundering Nine people have been arrested in connection with a coordinated law enforcement operation…