Category: TheHackerNews
Jan 11, 2024NewsroomVulnerability / Cyber Attack Cybersecurity researchers have developed a proof-of-concept (PoC) code that exploits a recently disclosed critical…
Jan 11, 2024NewsroomMalvertising / Cyber Attacks Cybersecurity researchers have identified an updated version of a macOS information stealer called Atomic…
Generative AI will enable anyone to launch sophisticated phishing attacks that only Next-generation MFA devices can stop The least surprising…
Jan 11, 2024NewsroomVulnerability / Patch Management Cisco has released software updates to address a critical security flaw impacting Unity Connection…
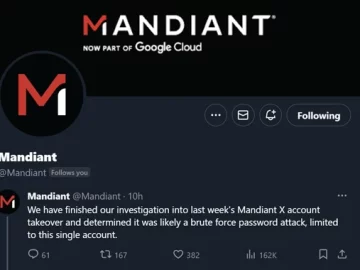
Jan 11, 2024NewsroomOnline Security / Cryptocurrency The compromise of Mandiant’s X (formerly Twitter) account last week was likely the result…
Jan 11, 2024NewsroomCybersecurity / Zero-Day A pair of zero-day flaws identified in Ivanti Connect Secure (ICS) and Policy Secure have…
Jan 10, 2024NewsroomServer Security / Cryptocurrency A new Mirai-based botnet called NoaBot is being used by threat actors as part…
Jan 10, 2024NewsroomRansomware / Data Security A decryptor for the Tortilla variant of the Babuk ransomware has been released by…
IT professionals have developed a sophisticated understanding of the enterprise attack surface – what it is, how to quantify it…
Jan 10, 2024NewsroomPrivacy / Regulatory Compliance The U.S. Federal Trade Commission (FTC) on Tuesday prohibited data broker Outlogic, which was…
Jan 10, 2024NewsroomVulnerability / Windows Security Microsoft has addressed a total of 48 security flaws spanning its software as part…
Jan 10, 2024NewsroomPatch Management / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added six security flaws…