Category: TheHackerNews
Follow this real-life network attack simulation, covering 6 steps from Initial Access to Data Exfiltration. See how attackers remain undetected…
Apr 25, 2024NewsroomCryptocurrency / Cybercrime The U.S. Department of Justice (DoJ) on Wednesday announced the arrest of two co-founders of…
Apr 25, 2024NewsroomVulnerability / Zero-Day A new malware campaign leveraged two zero-day flaws in Cisco networking gear to deliver custom…
Apr 25, 2024NewsroomTechnology / Privacy Google has once again pushed its plans to deprecate third-party tracking cookies in its Chrome…
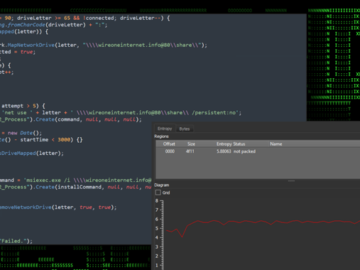
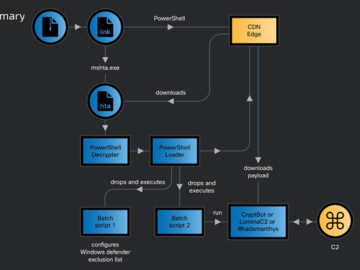
Apr 24, 2024NewsroomMalware / Endpoint Security Cybersecurity researchers have discovered an ongoing attack campaign that’s leveraging phishing emails to deliver…
Apr 24, 2024NewsroomCyber Attack / Cyber Espionage The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) on Monday sanctioned…
Apr 24, 2024NewsroomEncryption / Mobile Security Security vulnerabilities uncovered in cloud-based pinyin keyboard apps could be exploited to reveal users’…
A new malware campaign has been exploiting the updating mechanism of the eScan antivirus software to distribute backdoors and cryptocurrency…
Apr 24, 2024NewsroomMalware / Data Security A new ongoing malware campaign has been observed distributing three different stealers, such as…
Apr 23, 2024NewsroomSupply Chain Attack / Application Security Researchers have identified a dependency confusion vulnerability impacting an archived Apache project…
Apr 23, 2024The Hacker NewsThreat Hunting / Software Security In the high-stakes world of cybersecurity, the battleground has shifted. Supply…
Apr 23, 2024NewsroomCounterintelligence / National Security German authorities said they have issued arrest warrants against three citizens on suspicion of…