Category: TheHackerNews
Nov 04, 2025Ravie LakshmananVulnerability / Supply Chain Security Details have emerged about a now-patched critical security flaw in the popular…
Nov 04, 2025Ravie Lakshmanan Cybersecurity researchers have disclosed details of four security flaws in Microsoft Teams that could have exposed…
Nov 04, 2025Ravie LakshmananMalware / Cyber Espionage Threat actors are leveraging weaponized attachments distributed via phishing emails to deliver malware…
Nov 04, 2025Ravie LakshmananRansomware / Cybercrime Federal prosecutors in the U.S. have accused a trio of allegedly hacking the networks…
Nov 04, 2025Ravie LakshmananArtificial Intelligence / Vulnerability Google’s artificial intelligence (AI)-powered cybersecurity agent called Big Sleep has been credited by…
Nov 04, 2025Ravie LakshmananArtificial Intelligence / Malware Microsoft has disclosed details of a novel backdoor dubbed SesameOp that uses OpenAI…
Nov 04, 2025Ravie LakshmananArtificial Intelligence / Malware Microsoft has disclosed details of a novel backdoor dubbed SesameOp that uses OpenAI…
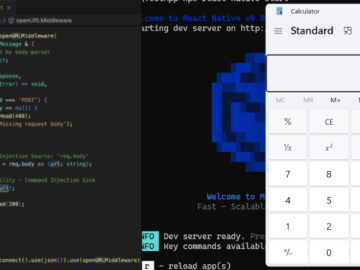
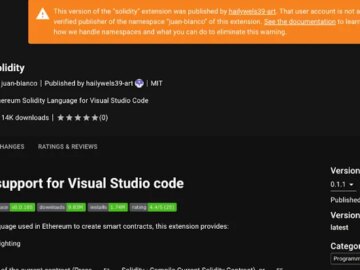
Nov 03, 2025Ravie LakshmananCryptocurrency / Threat Intelligence Cybersecurity researchers have flagged a new malicious extension in the Open VSX registry…
Nov 03, 2025Ravie LakshmananCybercrime / Supply Chain Attack Bad actors are increasingly training their sights on trucking and logistics companies…
Nov 03, 2025The Hacker NewsSOC Operations / Exposure Management Security Operations Centers (SOC) today are overwhelmed. Analysts handle thousands of…
Cybersecurity researchers have shed light on two different Android trojans called BankBot-YNRK and DeliveryRAT that are capable of harvesting sensitive…
Nov 03, 2025Ravie LakshmananCybersecurity / Malware The North Korea-linked threat actor known as Kimsuky has distributed a previously undocumented backdoor…