Category: TheHackerNews
Nov 01, 2025Ravie LakshmananArtificial Intelligence / Vulnerability The Australian Signals Directorate (ASD) has issued a bulletin about ongoing cyber attacks…
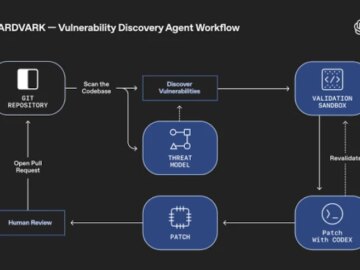
Oct 31, 2025Ravie LakshmananArtificial Intelligence / Code Security OpenAI has announced the launch of an “agentic security researcher” that’s powered…
Oct 31, 2025Ravie LakshmananMalware / Browser Security A suspected nation-state threat actor has been linked to the distribution of a…
Oct 31, 2025Ravie LakshmananEndpoint Security / Cyber Espionage The exploitation of a recently disclosed critical security flaw in Motex Lanscope…
Oct 31, 2025Ravie LakshmananMalware / Threat Intelligence A China-affiliated threat actor known as UNC6384 has been linked to a fresh…
Oct 31, 2025The Hacker NewsBusiness Continuity / Risk Management MSPs are facing rising client expectations for strong cybersecurity and compliance…
Oct 31, 2025Ravie LakshmananVulnerability / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and National Security Agency (NSA),…
Oct 31, 2025Ravie LakshmananMalware / Secure Coding Eclipse Foundation, which maintains the open-source Open VSX project, said it has taken…
Oct 31, 2025Ravie LakshmananVulnerability / Cyber Attack The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a high-severity…
Oct 31, 2025The Hacker NewsEndpoint Security / Network Security A design firm is editing a new campaign video on a…
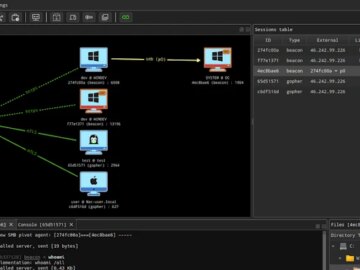
Oct 30, 2025Ravie LakshmananMalware / Cybercrime The open-source command-and-control (C2) framework known as AdaptixC2 is being used by a growing…
Google on Thursday revealed that the scam defenses built into Android safeguard users around the world from more than 10…