Category: TheHackerNews
Sep 29, 2023THNVulnerability / Network Security Cisco is warning of attempted exploitation of a security flaw in its IOS Software…
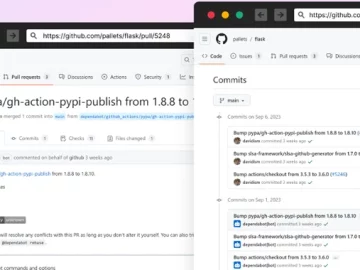
Sep 28, 2023THNSupply Chain / Malware A new malicious campaign has been observed hijacking GitHub accounts and committing malicious code…
Cybersecurity agencies from Japan and the U.S. have warned of attacks mounted by a state-backed hacking group from China to…
Sep 28, 2023The Hacker NewsBrowser Security / Cybersecurity The landscape of browser security has undergone significant changes over the past…
Sep 28, 2023THNMalware / Cyber Threat Government and telecom entities have been subjected to a new wave of attacks by…
Sep 28, 2023THNZero Day / Vulnerability Google on Wednesday rolled out fixes to address a new actively exploited zero-day in…
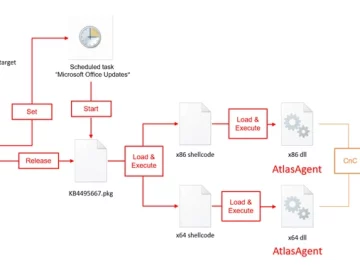
Sep 27, 2023THNMalware / Cyber Attack A new threat actor known as AtlasCross has been observed leveraging Red Cross-themed phishing…
Sep 27, 2023THNVulnerability / Endpoint Security A novel side-channel attack called GPU.zip renders virtually all modern graphics processing units (GPU)…
Data security is in the headlines often, and it’s almost never for a positive reason. Major breaches, new ways to…
Sep 27, 2023THNMalware / Cyber Threat A new malware strain called ZenRAT has emerged in the wild that’s distributed via…
Sep 27, 2023THNZero Day / Vulnerability Google has assigned a new CVE identifier for a critical security flaw in the…
Sep 26, 2023THNEndpoint Security / Password Microsoft is officially rolling out support for passkeys in Windows 11 today as part…