Category: TheHackerNews
Sep 06, 2023THNZero Day / Mobile Security Google has rolled out monthly security patches for Android to address a number…
Sep 06, 2023The Hacker NewsSecurity Operations Center (SOC) The role of the CISO keeps taking center stage as a business…
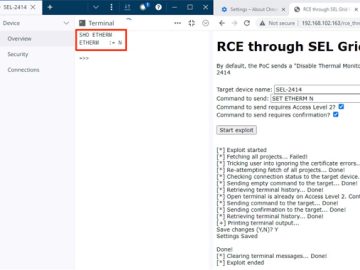
Sep 06, 2023THNVulnerability / ICS Nine security flaws have been disclosed in electric power management products made by Schweitzer Engineering…
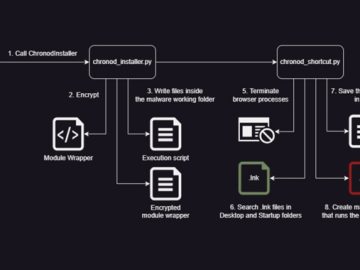
Sep 06, 2023THNCyber Crime / Email Security A previously undocumented “phishing empire” has been linked to cyber attacks aimed at…
Sep 06, 2023THNCyber Attack / Critical Infrastructure The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday said it thwarted…
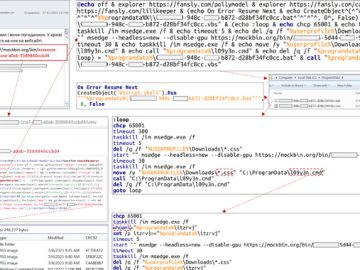
Sep 05, 2023THNCyber Attack / Malware The North Korean threat actor known as Andariel has been observed employing an arsenal…
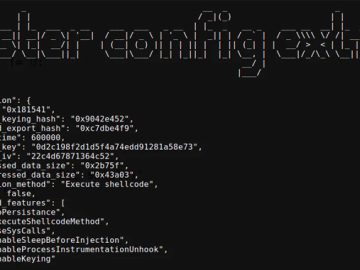
Sep 05, 2023THNCyber Threat / Malware An updated version of a malware loader known as BLISTER is being used as…
Sep 05, 2023The Hacker NewsData Breach / Password Security IBM’s 2023 installment of their annual “Cost of a Breach” report…
Sep 05, 2023The Hacker NewsAttack Surface / Identity Threats In today’s digital age, it’s not just about being online but…
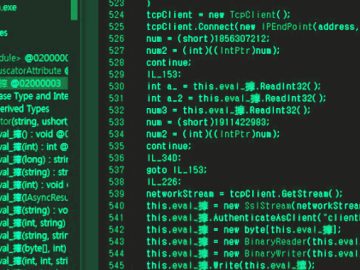
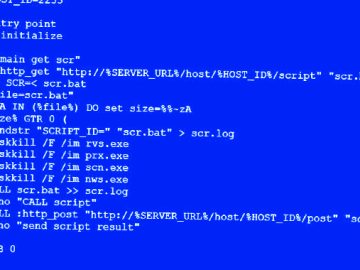
Sep 05, 2023THNCyber Threat / Malware Banking and logistics industries are under the onslaught of a reworked variant of a…
Sep 05, 2023THNSocial Media / Disinformation Meta has disclosed that it disrupted two of the largest known covert influence operations…
Sep 04, 2023THNVulnerability / Server Security An unknown threat actor has been observed weaponizing high-severity security flaws in the MinIO…