Category: TheHackerNews
Aug 17, 2023THNCyber Attack / Malware An ongoing cyber attack campaign originating from China is targeting the Southeast Asian gambling…
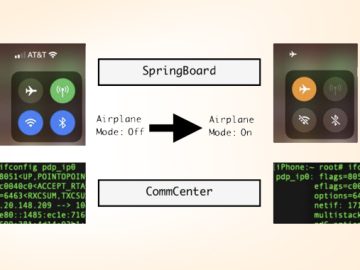
Aug 17, 2023THNMobile Security / Vulnerability Cybersecurity researchers have documented a novel post-exploit persistence technique on iOS 16 that could…
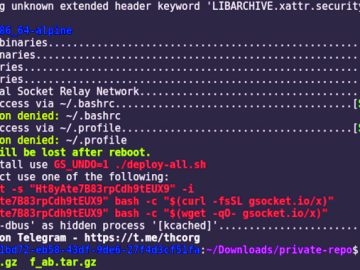
Aug 17, 2023THNCryptojacking / Proxyjacking A new, financially motivated operation dubbed LABRAT has been observed weaponizing a now-patched critical flaw…
Changes in the way we work have had significant implications for cybersecurity, not least in network monitoring. Workers no longer…
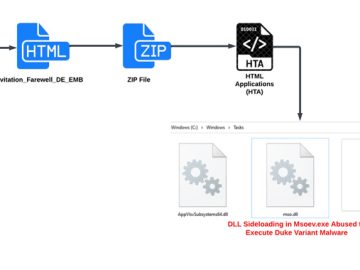
Aug 17, 2023THNCyber Espionage / Malware An ongoing campaign targeting ministries of foreign affairs of NATO-aligned countries points to the…
Aug 17, 2023THNVulnerability / Enterprise Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw…
Aug 16, 2023THNPassword Security / Encryption Google on Tuesday announced the first quantum resilient FIDO2 security key implementation as part…
Aug 16, 2023The Hacker NewsBrowser Security/ Online Security More and more organizations are choosing Google Workspace as their default employee…
Aug 16, 2023THNWindows Security / Supply Chain Active flaws in the PowerShell Gallery could be weaponized by threat actors to…
Aug 16, 2023The Hacker News At a little overt halfway through 2023, credential theft is still a major thorn in…
Aug 16, 2023THNSoftware Security / Cyber Threat Multiple critical security flaws have been reported in Ivanti Avalanche, an enterprise mobile…
Aug 16, 2023THNVulnerability / Enterprise Security Nearly 2,000 Citrix NetScaler instances have been compromised with a backdoor by weaponizing a…