Category: TheHackerNews
Aug 07, 2023The Hacker NewsSIEM and XDR Platform In today’s interconnected world, evolving security solutions to meet growing demand is…
Aug 07, 2023THNCyber Crime / Cryptocurrency The U.S. Federal Bureau of Investigation (FBI) is warning about cyber crooks masquerading as…
Aug 05, 2023THNLinux / Malware Threat actors are using an open-source rootkit called Reptile to target Linux systems in South…
Aug 05, 2023The Hacker NewsManaged Detection and Response Managed Detection and Response (MDR) has emerged as a crucial solution for…
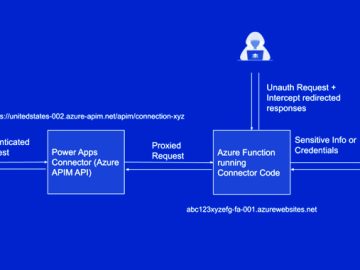
Aug 05, 2023THNVulnerability / Cyber Threat Microsoft on Friday disclosed that it has addressed a critical security flaw impacting Power…
Aug 05, 2023THNVulnerability / Software Security Cybersecurity researchers have discovered a new high-severity security flaw in PaperCut print management software…
Aug 04, 2023THNCryptocurrency / Cyber Crime A married couple from New York City has pleaded guilty to money laundering charges…
Aug 04, 2023The Hacker News Privileged Access Management (PAM) solutions are widely acknowledged as the gold standard for securing critical…
Cybersecurity researchers have discovered a new bunch of malicious packages on the npm package registry that are designed to exfiltrate…
Aug 04, 2023THNSoftware Security / Cyber Theat A four-year-old critical security flaw impacting Fortinet FortiOS SSL has emerged as one…
Aug 03, 2023THNMobile Security / Malware Threat actors are leveraging a technique called versioning to evade Google Play Store’s malware…
Aug 03, 2023THNVulnerability / Cyber Threat Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by malicious actors…