Category: TheHackerNews
The healthcare industry is under a constant barrage of cyberattacks. It has traditionally been one of the most frequently targeted…
Jul 24, 2023THNMobile Security / Privacy Google has announced that it intends to add support for Message Layer Security (MLS)…
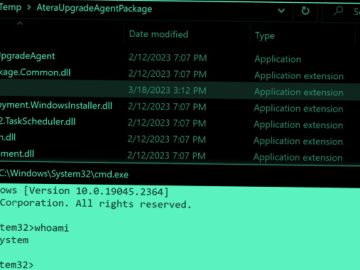
Jul 24, 2023THNWindows Security / Zero-Day Zero-day vulnerabilities in Windows Installers for the Atera remote monitoring and management software could…
Jul 24, 2023THNLinux / Network Security Details have emerged about a now-patched flaw in OpenSSH that could be potentially exploited…
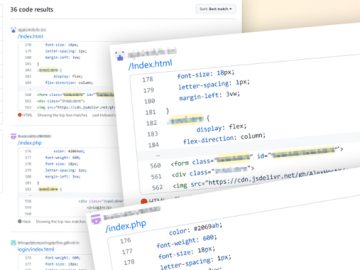
Jul 24, 2023THNSupply Chain / Cyber Attack Cybersecurity researchers said they have discovered what they say is the first open-source…
Jul 22, 2023THNEncryption / Privacy Apple has warned that it would rather stop offering iMessage and FaceTime services in the…
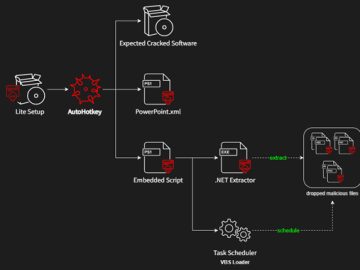
Jul 21, 2023THNMalware / Software Security A new variant of AsyncRAT malware dubbed HotRat is being distributed via free, pirated…
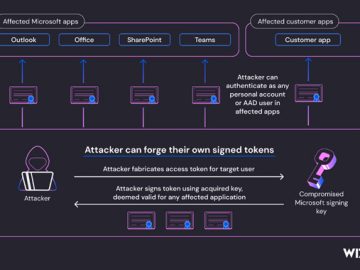
Jul 21, 2023THNEmail Security / Cyber Attack The recent attack against Microsoft’s email infrastructure by a Chinese nation-state actor referred…
Jul 21, 2023The Hacker NewsPassword Security / Cybersecurity Regardless of the country, local government is essential in most citizens’ lives….
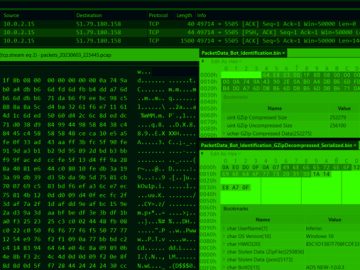
Jul 21, 2023THNCyber Threat / Malware A new malware strain known as BundleBot has been stealthily operating under the radar…
Jul 21, 2023THNVulnerability / Botnet Several distributed denial-of-service (DDoS) botnets have been observed exploiting a critical flaw in Zyxel devices…
Jul 21, 2023THNVulnerability / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an advisory on Thursday warning…