Category: TheHackerNews
Jul 03, 2023Ravie LakshmananMalware / Hacking In yet another sign of a lucrative crimeware-as-a-service (CaaS) ecosystem, cybersecurity researchers have discovered…
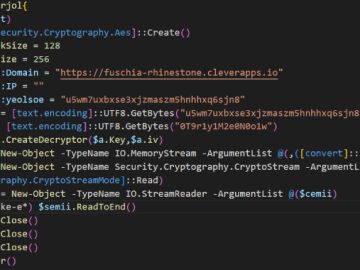
Threat actors associated with the BlackCat ransomware have been observed employing malvertising tricks to distribute rogue installers of the WinSCP…
Jul 01, 2023Ravie LakshmananWebsite Security / Cyber Threat As many as 200,000 WordPress websites are at risk of ongoing attacks…
Jul 01, 2023Ravie LakshmananEndpoint Security / Malware Researchers have pulled back the curtain on an updated version of an Apple…
Jun 30, 2023The Hacker NewsCyber Espionage/ Malware Charming Kitten, the nation-state actor affiliated with Iran’s Islamic Revolutionary Guard Corps (IRGC),…
Jun 30, 2023The Hacker NewsSaaS Security / Artificial Intelligence, In today’s fast-paced digital landscape, the widespread adoption of AI (Artificial…
Jun 30, 2023Ravie LakshmananServer Security / Cyber Threat An active financially motivated campaign is targeting vulnerable SSH servers to covertly…
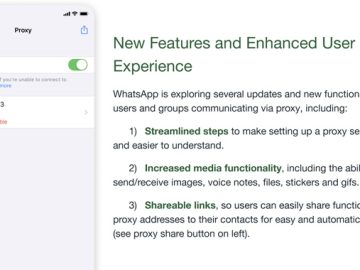
Jun 30, 2023Ravie LakshmananPrivacy / Tech Meta’s WhatsApp has rolled out updates to its proxy feature, allowing more flexibility in…
Jun 30, 2023Ravie LakshmananVulnerability / Software Security MITRE has released its annual list of the Top 25 “most dangerous software…
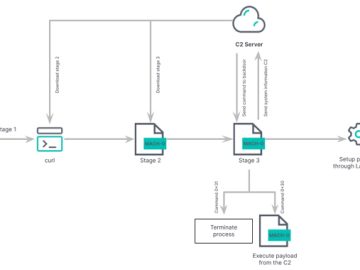
Jun 29, 2023Ravie Lakshmanan The Iranian state-sponsored group dubbed MuddyWater has been attributed to a previously unseen command-and-control (C2) framework…
Jun 29, 2023Ravie LakshmananMobile Security / Malware Cybersecurity researchers have shared the inner workings of an Android malware family called…
Jun 29, 2023Ravie LakshmananMobile Security / Privacy Android-based phone monitoring app LetMeSpy has disclosed a security breach that allowed an…