Category: TheHackerNews
Every October brings a familiar rhythm – pumpkin-spice everything in stores and cafés, alongside a wave of reminders, webinars, and…
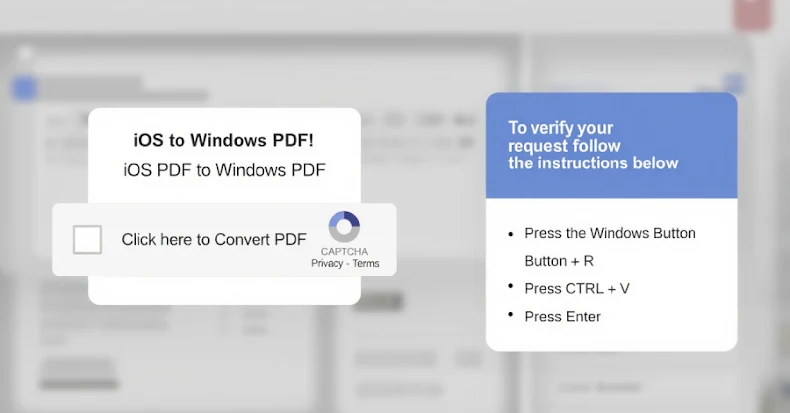
Oct 14, 2025Ravie LakshmananMalware / Social Engineering Cybersecurity researchers have shed light on a previously undocumented threat actor called TA585…
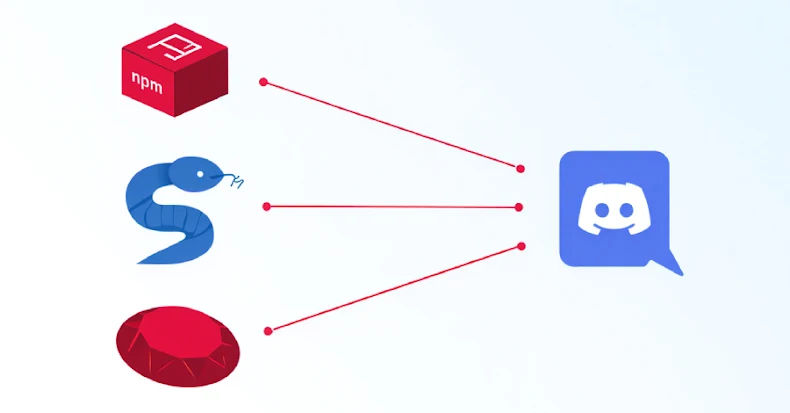
Oct 14, 2025Ravie LakshmananMalware / Typosquatting Cybersecurity researchers have identified several malicious packages across npm, Python, and Ruby ecosystems that…
Think your WAF has you covered? Think again. This holiday season, unmonitored JavaScript is a critical oversight allowing attackers to…
Oct 13, 2025Ravie LakshmananBrowser Security / Windows Security Microsoft said it has revamped the Internet Explorer (IE) mode in its…
Malware campaigns distributing the RondoDox botnet have expanded their targeting focus to exploit more than 50 vulnerabilities across over 30…
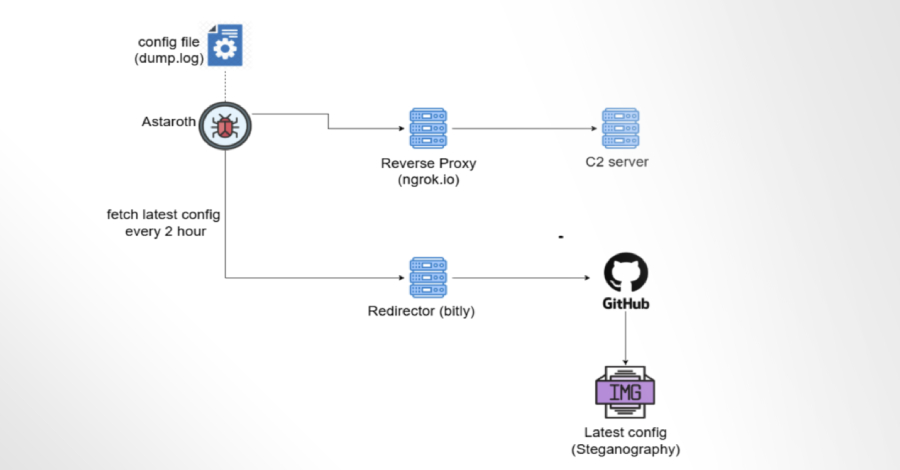
Oct 13, 2025Ravie LakshmananMalware / Financial Security Cybersecurity researchers are calling attention to a new campaign that delivers the Astaroth…
Oct 13, 2025Ravie LakshmananRansomware / Windows Security Cybersecurity researchers have disclosed details of a new Rust-based backdoor called ChaosBot that…
Oct 12, 2025Ravie LakshmananVulnerability / Threat Intelligence Oracle on Saturday issued a security alert warning of a fresh security flaw…
Oct 11, 2025Ravie LakshmananCloud Security / Network Security Cybersecurity company Huntress on Friday warned of “widespread compromise” of SonicWall SSL…
Oct 11, 2025Ravie LakshmananNetwork Security / Vulnerability Threat actors are abusing Velociraptor, an open-source digital forensics and incident response (DFIR)…
Oct 10, 2025Ravie LakshmananSaaS Security / Threat Intelligence A threat actor known as Storm-2657 has been observed hijacking employee accounts…