Category: TheHackerNews
Web applications, often in the form of Software as a Service (SaaS), are now the cornerstone for businesses all over…
A previously undocumented Android malware campaign has been observed leveraging money-lending apps to blackmail victims into paying up with personal…
Dec 15, 2022Ravie LakshmananWindows Security / Network Security Microsoft has revised the severity of a security vulnerability it originally patched…
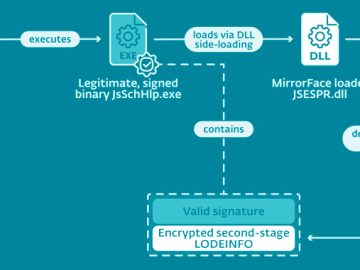
Dec 15, 2022Ravie LakshmananAdvanced Persistent Threat A Chinese-speaking advanced persistent threat (APT) actor codenamed MirrorFace has been attributed to a…
Dec 16, 2022Ravie LakshmananBackup & Recovery / Zero-Day The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities…
Dec 16, 2022Ravie LakshmananServer Security / Botnet Microsoft on Thursday flagged a cross-platform botnet that’s primarily designed to launch distributed…
Dec 16, 2022Ravie LakshmananEncryption / Data Security The U.S. National Institute of Standards and Technology (NIST), an agency within the…
Dec 16, 2022Ravie LakshmananSecure Coding / Code Hosting GitHub on Thursday said it is making available its secret scanning service…
Dec 27, 2022Ravie LakshmananCyber Attack / Windows Security BlueNoroff, a subcluster of the notorious Lazarus Group, has been observed adopting…
Reality has a way of asserting itself, irrespective of any personal or commercial choices we make, good or bad. For…
Dec 16, 2022Ravie LakshmananCyber Espionage / Privacy A former Twitter employee who was found guilty of spying on behalf of…
Government entities in Ukraine have been breached as part of a new campaign that leveraged trojanized versions of Windows 10…