Category: TheHackerNews
Cybersecurity researchers have discovered a new malware loader codenamed CountLoader that has been put to use by Russian ransomware gangs…
AI’s growing role in enterprise environments has heightened the urgency for Chief Information Security Officers (CISOs) to drive effective AI…
Sep 18, 2025Ravie LakshmananMalware / Supply Chain Attack Cybersecurity researchers have discovered two new malicious packages in the Python Package…
Sep 18, 2025Ravie LakshmananVulnerability / Browser Security Google on Wednesday released security updates for the Chrome web browser to address…
The threat actor known as TA558 has been attributed to a fresh set of attacks delivering various remote access trojans…
Sep 17, 2025Ravie LakshmananCyber Espionage / Malware A China-aligned threat actor known as TA415 has been attributed to spear-phishing campaigns…
Sep 17, 2025The Hacker NewsCyber Resilience / Webinar Quantum computing and AI working together will bring incredible opportunities. Together, the…
Sep 17, 2025The Hacker NewsAI Security / Shadow IT Generative AI has gone from a curiosity to a cornerstone of…
Sep 17, 2025Ravie LakshmananThreat Intelligence / Cybercrime Cybersecurity researchers have tied a fresh round of cyber attacks targeting financial services…
Sep 17, 2025Ravie LakshmananData Breach / Cybercrime The U.S. Department of Justice (DoJ) on Tuesday resentenced the former administrator of…
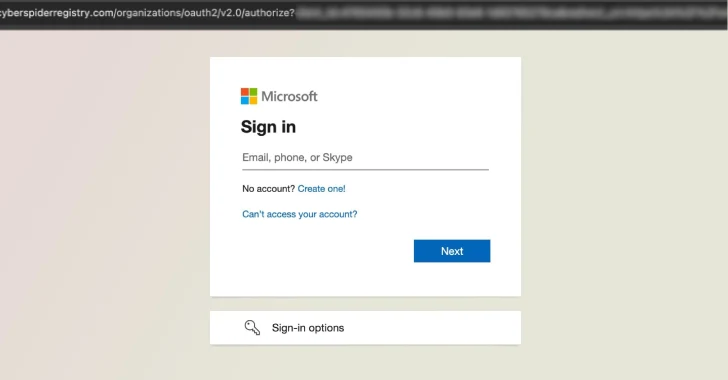
Microsoft’s Digital Crimes Unit said it teamed up with Cloudflare to coordinate the seizure of 338 domains used by RaccoonO365,…
Sep 16, 2025Ravie LakshmananVulnerability / Cloud Security Cybersecurity researchers have disclosed multiple critical security vulnerabilities in Chaos Mesh that, if…