Category: TheHackerNews
Sep 16, 2025Ravie LakshmananAd Fraud / Mobile Security A massive ad fraud and click fraud operation dubbed SlopAds ran a…
Sep 16, 2025Ravie LakshmananMalware / Social Engineering Cybersecurity researchers have warned of a new campaign that’s leveraging a variant of…
Sep 16, 2025The Hacker NewsAI Security / Enterprise Security AI agents are rapidly becoming a core part of the enterprise,…
Sep 16, 2025Ravie LakshmananVulnerability / Spyware Apple on Monday backported fixes for a recently patched security flaw that has been…
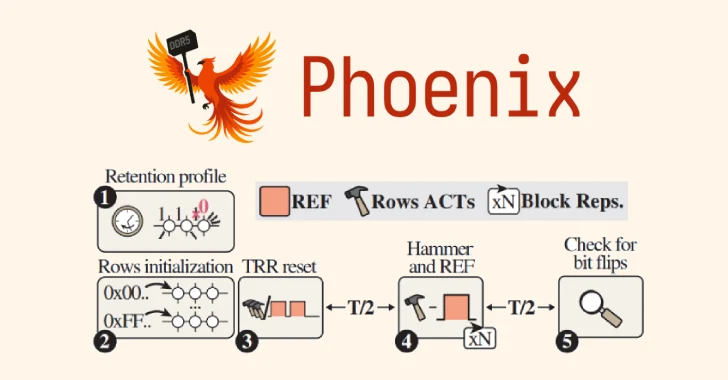
Sep 16, 2025Ravie LakshmananHardware Security / Vulnerability A team of academics from ETH Zürich and Google has discovered a new…
Sep 16, 2025Ravie LakshmananMalware / Cyber Attack Cybersecurity researchers have flagged a fresh software supply chain attack targeting the npm…
Sep 15, 2025Ravie LakshmananMalware / Network Security The China-aligned threat actor known as Mustang Panda has been observed using an…
Attacks that target users in their web browsers have seen an unprecedented rise in recent years. In this article, we’ll…
A new artificial intelligence (AI)-powered penetration testing tool linked to a China-based company has attracted nearly 11,000 downloads on the…
Chinese-speaking users are the target of a search engine optimization (SEO) poisoning campaign that uses fake software sites to distribute…
The U.S. Federal Bureau of Investigation (FBI) has issued a flash alert to release indicators of compromise (IoCs) associated with…
Sep 12, 2025Ravie Lakshmanan Apple has notified users in France of a spyware campaign targeting their devices, according to the…