Category: TheHackerNews
Sep 12, 2025Ravie LakshmananVulnerability / Mobile Security Samsung has released its monthly security updates for Android, including a fix for…
Sep 12, 2025Ravie LakshmananVulnerability / Cyber Espionage The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical…
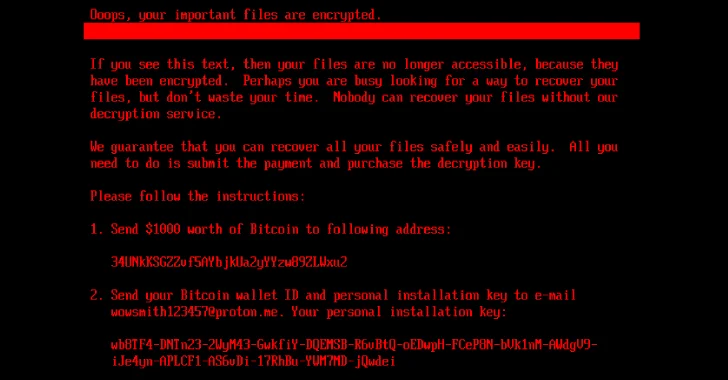
Cybersecurity researchers have discovered a new ransomware strain dubbed HybridPetya that resembles the notorious Petya/NotPetya malware, while also incorporating the…
The security landscape for cloud-native applications is undergoing a profound transformation. Containers, Kubernetes, and serverless technologies are now the default…
A security weakness has been disclosed in the artificial intelligence (AI)-powered code editor Cursor that could trigger code execution when…
U.S. Senator Ron Wyden has called on the Federal Trade Commission (FTC) to probe Microsoft and hold it responsible for…
Sep 11, 2025Ravie LakshmananArtificial Intelligence / Mobile Security Google on Tuesday announced that its new Google Pixel 10 phones support…
Threat actors affiliated with the Akira ransomware group have continued to target SonicWall devices for initial access. Cybersecurity firm Rapid7…
Sep 11, 2025The Hacker NewsContinuous Threat Exposure Management CISOs know their field. They understand the threat landscape. They understand how…
Sep 11, 2025Ravie LakshmananMalvertising / Browser Security Cybersecurity researchers have disclosed two new campaigns that are serving fake browser extensions…
Sep 11, 2025Ravie LakshmananMalware / Credential Theft Cybersecurity researchers have disclosed details of a new campaign that leverages ConnectWise ScreenConnect,…
Sep 10, 2025Ravie LakshmananCybersecurity / Malware An advanced persistent threat (APT) group from China has been attributed to the compromise…