Category: TheHackerNews
Sep 05, 2025The Hacker NewsPentesting / Security Operations Pentesting remains one of the most effective ways to identify real-world security…
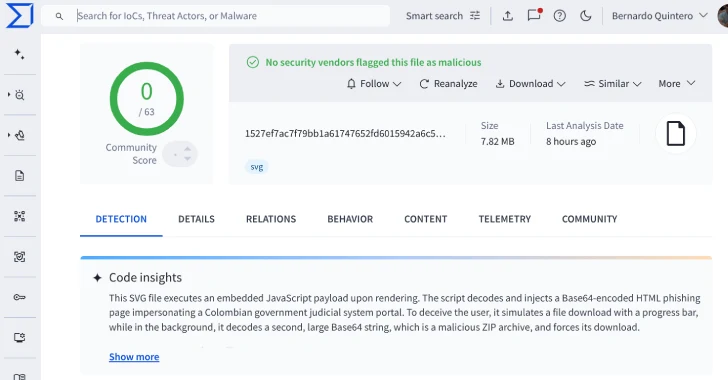
Sep 05, 2025Ravie LakshmananMalware / Cryptocurrency Cybersecurity researchers have flagged a new malware campaign that has leveraged Scalable Vector Graphics…
Cybersecurity researchers have lifted the lid on a previously undocumented threat cluster dubbed GhostRedirector that has managed to compromise at…
Sep 04, 2025Ravie LakshmananCybersecurity / Malware The Russian state-sponsored hacking group tracked as APT28 has been attributed to a new…
Sep 04, 2025Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added two security…
Sep 04, 2025Ravie LakshmananGDPR / Data Privacy The French data protection authority has fined Google and Chinese e-commerce giant Shein…
Sep 04, 2025Ravie LakshmananArtificial Intelligence / Malware Cybersecurity researchers have flagged a new technique that cybercriminals have adopted to bypass…
Sep 03, 2025Ravie LakshmananMalware / Social Engineering Cybersecurity researchers have discovered two new malicious packages on the npm registry that…
Sep 03, 2025Ravie LakshmananMobile Security / Vulnerability Google has shipped security updates to address 120 security flaws in its Android…
In January 2025, cybersecurity experts at Wiz Research found that Chinese AI specialist DeepSeek had suffered a data leak, putting…
Sep 03, 2025Ravie LakshmananArtificial Intelligence / Vulnerability Threat actors are attempting to leverage a newly released artificial intelligence (AI) offensive…
Sep 03, 2025Ravie LakshmananData Breach / Cyber Espionage An Iran-nexus group has been linked to a “coordinated” and “multi-wave” spear-phishing…