Category: TheHackerNews
Cybersecurity researchers have called attention to a cyber attack in which unknown threat actors deployed an open-source endpoint monitoring and…
Aug 30, 2025Ravie LakshmananZero-Day / Vulnerability WhatsApp has addressed a security vulnerability in its messaging apps for Apple iOS and…
Aug 29, 2025Ravie LakshmananVulnerability / Web Security Three new security vulnerabilities have been disclosed in the Sitecore Experience Platform that…
An abandoned update server associated with input method editor (IME) software Sogou Zhuyin was leveraged by threat actors as part…
Aug 29, 2025Ravie LakshmananThreat Intelligence / Malware Amazon on Friday said it flagged and disrupted what it described as an…
Aug 29, 2025The Hacker NewsEnterprise Security / Artificial Intelligence Generative AI platforms like ChatGPT, Gemini, Copilot, and Claude are increasingly…
Aug 29, 2025Ravie LakshmananZero-Day / Vulnerability The Sangoma FreePBX Security Team has issued an advisory warning about an actively exploited…
Aug 29, 2025Ravie LakshmananVulnerability / Enterprise Security Click Studios, the developer of enterprise-focused password management solution Passwordstate, said it has…
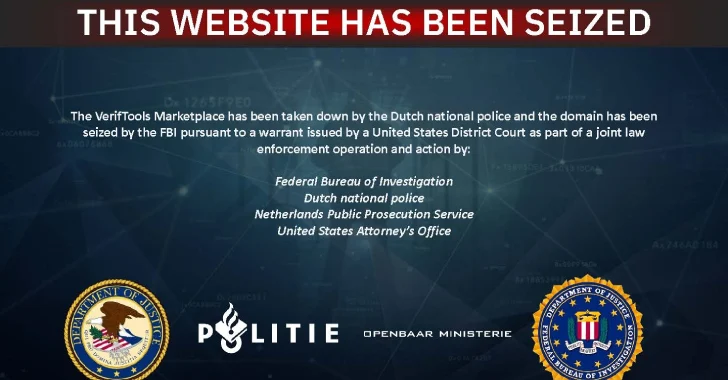
Aug 29, 2025Ravie LakshmananCryptocurrency / Cybercrime Authorities from the Netherlands and the United States have announced the dismantling of an…
Aug 29, 2025Ravie LakshmananData Breach / Salesforce Google has revealed that the recent wave of attacks targeting Salesforce instances via…
Aug 29, 2025Ravie LakshmananMalware / Windows Security Cybersecurity researchers have discovered a cybercrime campaign that’s using malvertising tricks to direct…
Aug 28, 2025Ravie LakshmananMalware / Ransomware Cybersecurity researchers have discovered a loophole in the Visual Studio Code Marketplace that allows…