Category: TheHackerNews
The China-linked advanced persistent threat (APT) actor known as Salt Typhoon has continued its attacks targeting networks across the world,…
The China-linked advanced persistent threat (APT) actor known as Salt Typhoon has continued its attacks targeting networks across the world,…
Aug 28, 2025The Hacker NewsCloud Security / Generative AI Picture this: Your team rolls out some new code, thinking everything’s…
Every day, businesses, teams, and project managers trust platforms like Trello, Asana, etc., to collaborate and manage tasks. But what…
The maintainers of the nx build system have alerted users to a supply chain attack that allowed attackers to publish…
Aug 28, 2025Ravie LakshmananArtificial Intelligence / Malware The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) announced…
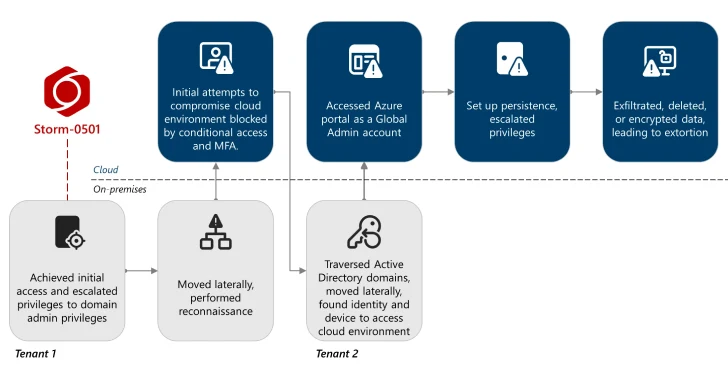
The financially motivated threat actor known as Storm-0501 has been observed refining its tactics to conduct data exfiltration and extortion…
Cybersecurity company ESET has disclosed that it discovered an artificial intelligence (AI)-powered ransomware variant codenamed PromptLock. Written in Golang, the…
Aug 27, 2025Ravie LakshmananCyber Attack / Artificial Intelligence Anthropic on Wednesday revealed that it disrupted a sophisticated operation that weaponized…
A threat activity cluster known as ShadowSilk has been attributed to a fresh set of attacks targeting government entities within…
Aug 27, 2025The Hacker NewsEnterprise Security / Data Protection Employees are experimenting with AI at record speed. They are drafting…
Cybersecurity researchers have discovered five distinct activity clusters linked to a persistent threat actor known as Blind Eagle between May…