Category: TheHackerNews
Aug 25, 2025Ravie LakshmananMalware / Cyber Attack The advanced persistent threat (APT) actor known as Transparent Tribe has been observed…
Aug 24, 2025Ravie LakshmananMalware / Supply Chain Security Cybersecurity researchers have discovered a malicious Go module that presents itself as…
Cybersecurity researchers are calling attention to multiple campaigns that leverage known security vulnerabilities and expose Redis servers to various malicious…
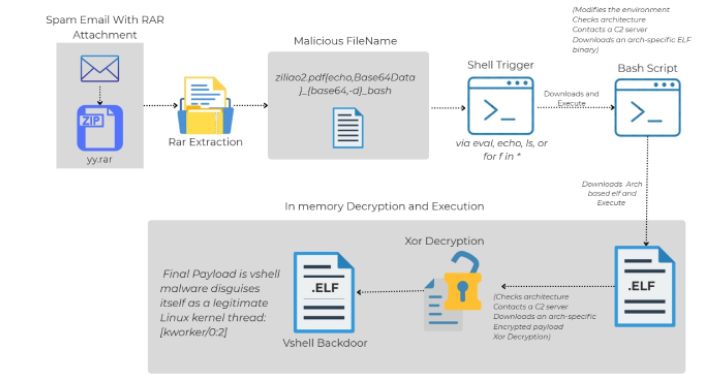
Cybersecurity researchers have shed light on a novel attack chain that employs phishing emails to deliver an open-source backdoor called…
Aug 22, 2025Ravie LakshmananOnline Fraud / Financial Crime INTERPOL on Friday announced that authorities from 18 countries across Africa have…
Cybersecurity researchers are calling attention to malicious activity orchestrated by a China-nexus cyber espionage group known as Murky Panda that…
Aug 22, 2025The Hacker NewsPenetration Testing / Security Operations Pentesting remains one of the most effective ways to identify real-world…
Aug 22, 2025The Hacker NewsPenetration Testing / Security Operations Pentesting remains one of the most effective ways to identify real-world…
Aug 22, 2025The Hacker NewsPenetration Testing / Security Operations Pentesting remains one of the most effective ways to identify real-world…
Aug 22, 2025Ravie LakshmananCybercrime / Malware A 55-year-old Chinese national has been sentenced to four years in prison and three…
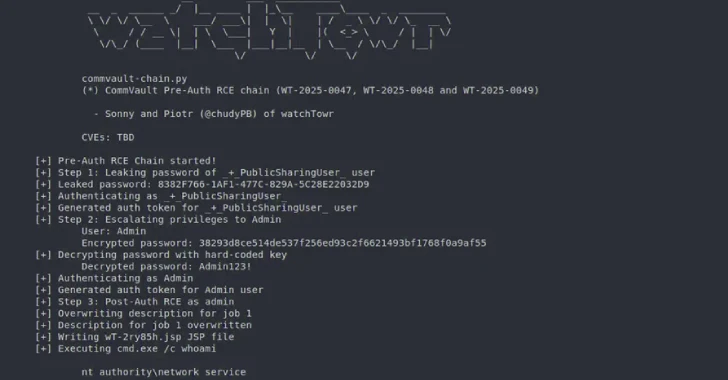
Aug 21, 2025Ravie LakshmananVulnerability / Software Security Commvault has released updates to address four security gaps that could be exploited…
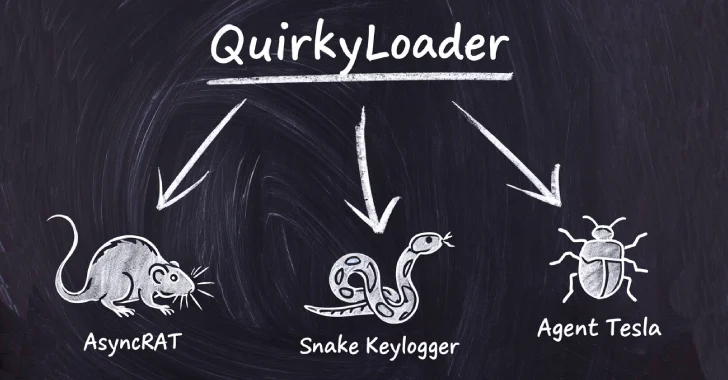
Aug 21, 2025Ravie LakshmananMalware / Email Security Cybersecurity researchers have disclosed details of a new malware loader called QuirkyLoader that’s…