Category: TheHackerNews
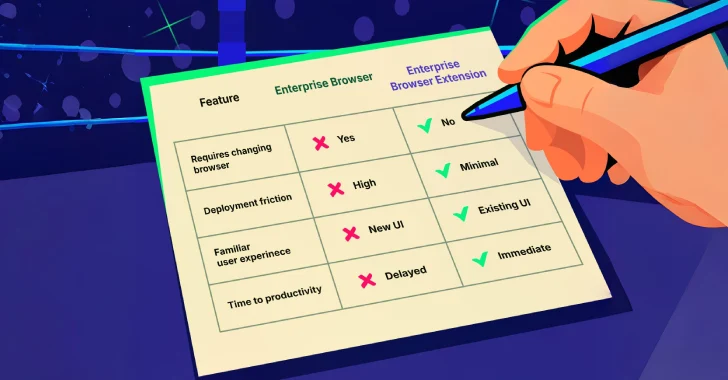
Aug 12, 2025The Hacker NewsBrowser Security / Zero Trust Most security tools can’t see what happens inside the browser, but…
Aug 12, 2025Ravie LakshmananVulnerability / Threat Intelligence The Dutch National Cyber Security Centre (NCSC-NL) has warned of cyber attacks exploiting…
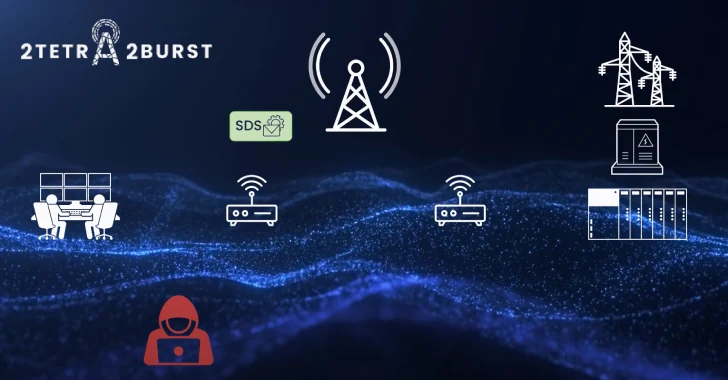
Aug 11, 2025Ravie LakshmananEncryption / Network Security Cybersecurity researchers have discovered a fresh set of security issues in the Terrestrial…
Aug 11, 2025Ravie LakshmananEncryption / Network Security Cybersecurity researchers have discovered a fresh set of security issues in the Terrestrial…
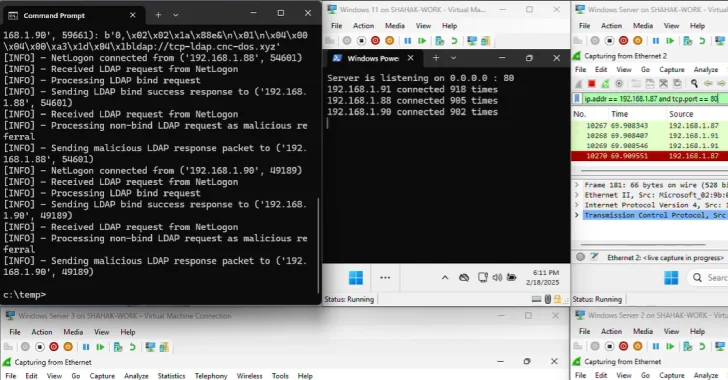
Aug 11, 2025Ravie LakshmananVulnerability / Network Security Malicious actors have been observed exploiting a now-patched critical security flaw impacting Erlang/Open…
Aug 11, 2025Ravie LakshmananVulnerability / Network Security Malicious actors have been observed exploiting a now-patched critical security flaw impacting Erlang/Open…
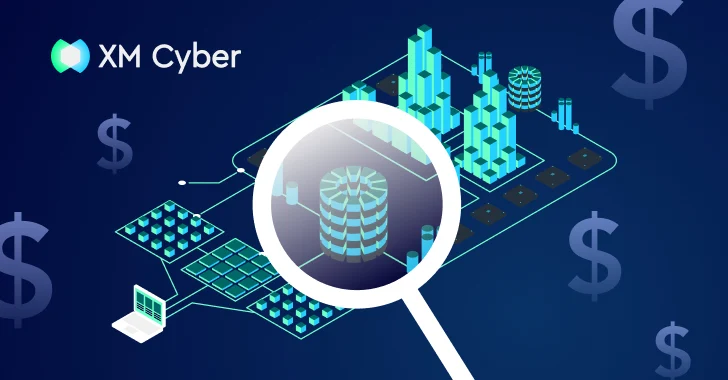
The Evolution of Exposure Management Most security teams have a good sense of what’s critical in their environment. What’s harder…
Aug 11, 2025Ravie LakshmananZero-Day / Vulnerability The maintainers of the WinRAR file archiving utility have released an update to address…
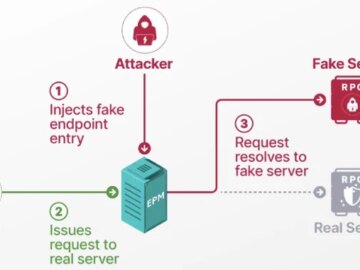
Aug 10, 2025Ravie LakshmananVulnerability / Network Security A novel attack technique could be weaponized to rope thousands of public domain…
Aug 10, 2025Ravie LakshmananVulnerability / Network Security A novel attack technique could be weaponized to rope thousands of public domain…
Aug 09, 2025Ravie LakshmananVulnerability / Hardware Security Cybersecurity researchers have uncovered multiple security flaws in Dell’s ControlVault3 firmware and its…
Aug 10, 2025Ravie LakshmananVulnerability / Endpoint Security Cybersecurity researchers have presented new findings related to a now-patched security issue in…