Category: TheHackerNews
Aug 09, 2025Ravie LakshmananVulnerability / Hardware Security Cybersecurity researchers have disclosed vulnerabilities in select model webcams from Lenovo that could…
Cybersecurity researchers have uncovered a jailbreak technique to bypass ethical guardrails erected by OpenAI in its latest large language model…
Cybersecurity researchers have discovered over a dozen vulnerabilities in enterprise secure vaults from CyberArk and HashiCorp that, if successfully exploited,…
Cybersecurity researchers are drawing attention to a new campaign that’s using legitimate generative artificial intelligence (AI)-powered website building tools like…
A fresh set of 60 malicious packages has been uncovered targeting the RubyGems ecosystem by posing as seemingly innocuous automation…
When an organization’s credentials are leaked, the immediate consequences are rarely visible—but the long-term impact is far-reaching. Far from the…
A newly discovered campaign dubbed GreedyBear has leveraged over 150 malicious extensions to the Firefox marketplace that are designed to…
Aug 07, 2025Ravie LakshmananMalware / Threat Intelligence The threat actors behind the SocGholish malware have been observed leveraging Traffic Distribution…
Aug 07, 2025Ravie LakshmananNetwork Security / Vulnerability SonicWall has revealed that the recent spike in activity targeting its Gen 7…
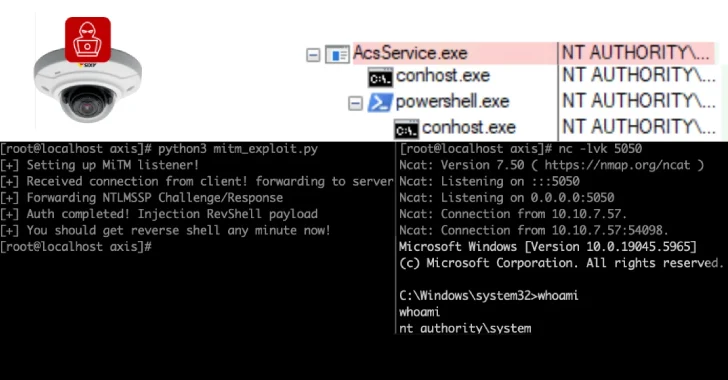
Aug 07, 2025Ravie LakshmananVulnerability / Threat Intelligence Cybersecurity researchers have disclosed multiple security flaws in video surveillance products from Axis…
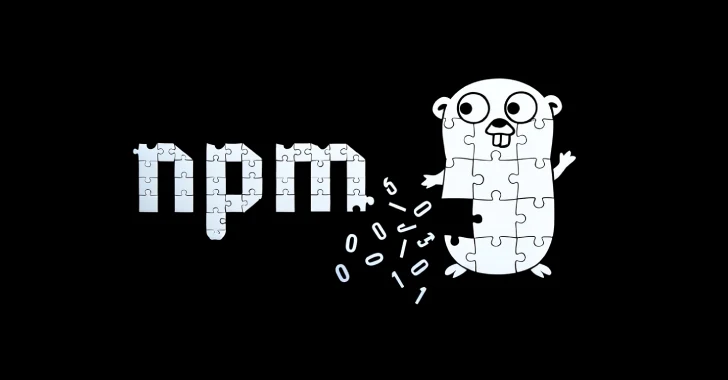
Aug 07, 2025Ravie LakshmananMalware / Threat Intelligence Cybersecurity researchers have discovered a set of 11 malicious Go packages that are…
Now that we are well into 2025, cloud attacks are evolving faster than ever and artificial intelligence (AI) is both…