Category: TheHackerNews
Aug 06, 2025Ravie LakshmananVulnerability / Firmware Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added three old…
When Technology Resets the Playing Field In 2015 I founded a cybersecurity testing software company with the belief that automated…
Aug 05, 2025Ravie LakshmananSocial Engineering / Malware A combination of propagation methods, narrative sophistication, and evasion techniques enabled the social…
Aug 05, 2025Ravie LakshmananAI Security / MCP Protocol Cybersecurity researchers have disclosed a high-severity security flaw in the artificial intelligence…
Aug 05, 2025Ravie LakshmananVulnerability / Mobile Security Google has released security updates to address multiple security flaws in Android, including…
In SaaS security conversations, “misconfiguration” and “vulnerability” are often used interchangeably. But they’re not the same thing. And misunderstanding that…
Why do SOC teams still drown in alerts even after spending big on security tools? False positives pile up, stealthy…
Aug 05, 2025Ravie LakshmananMalware / Mobile Security Cybersecurity researchers have lifted the veil on a widespread malicious campaign that’s targeting…
Aug 05, 2025Ravie LakshmananZero-Day / Network Security SonicWall said it’s actively investigating reports to determine if there is a new…
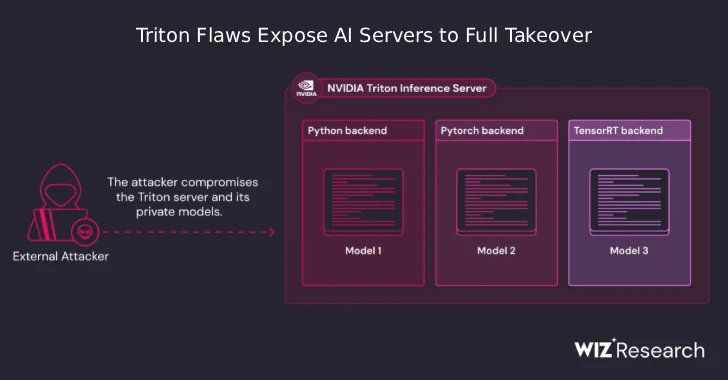
Aug 04, 2025Ravie LakshmananAI Security / Vulnerability A newly disclosed set of security flaws in NVIDIA’s Triton Inference Server for…
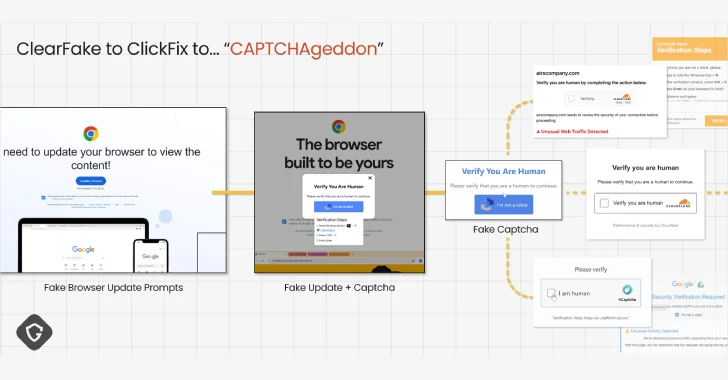
Aug 04, 2025Ravie LakshmananMalware / Browser Security Cybersecurity researchers are calling attention to a new wave of campaigns distributing a…
Some of the most devastating cyberattacks don’t rely on brute force, but instead succeed through stealth. These quiet intrusions often…