Category: TheHackerNews
Aug 21, 2025Ravie LakshmananVulnerability / Zero-Day Apple has released security updates to address a security flaw impacting iOS, iPadOS, and…
Aug 20, 2025Ravie LakshmananCyber Espionage / Vulnerability A Russian state-sponsored cyber espionage group known as Static Tundra has been observed…
Aug 20, 2025Ravie LakshmananVulnerability / Browser Security Popular password manager plugins for web browsers have been found susceptible to clickjacking…
Cybersecurity researchers have demonstrated a new prompt injection technique called PromptFix that tricks a generative artificial intelligence (GenAI) model into…
Cybersecurity researchers have demonstrated a new prompt injection technique called PromptFix that tricks a generative artificial intelligence (GenAI) model into…
Cybersecurity researchers have demonstrated a new prompt injection technique called PromptFix that tricks a generative artificial intelligence (GenAI) model into…
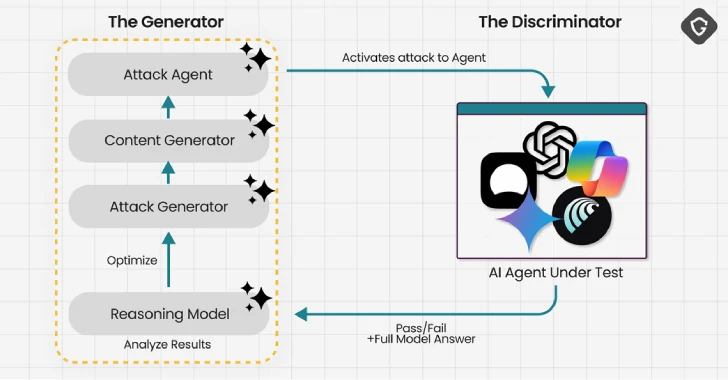
Aug 20, 2025The Hacker NewsArtificial Intelligence / Enterprise Security Do you know how many AI agents are running inside your…
Modern businesses face a rapidly evolving and expanding threat landscape, but what does this mean for your business? It means…
North Korean threat actors have been attributed to a coordinated cyber espionage campaign targeting diplomatic missions in their southern counterpart…
Aug 20, 2025Ravie LakshmananBotnet / Cybercrime A 22-year-old man from the U.S. state of Oregon has been charged with allegedly…
Aug 19, 2025Ravie LakshmananLinux / Malware Threat actors are exploiting a nearly two-year-old security flaw in Apache ActiveMQ to gain…
Aug 19, 2025Ravie LakshmananMalware / Cyber Attack Financial institutions like trading and brokerage firms are the target of a new…