Category: TheHackerNews
Until recently, the cyber attacker methodology behind the biggest breaches of the last decade or so has been pretty consistent:…
Jul 29, 2025Ravie LakshmananVulnerability / Software Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a high-severity…
Jul 28, 2025Ravie LakshmananMalware / Developer Tools In what’s the latest instance of a software supply chain attack, unknown threat…
Picture this: you’ve hardened every laptop in your fleet with real‑time telemetry, rapid isolation, and automated rollback. But the corporate…
Jul 28, 2025Ravie LakshmananCyber Attack / Ransomware The notorious cybercrime group known as Scattered Spider is targeting VMware ESXi hypervisors…
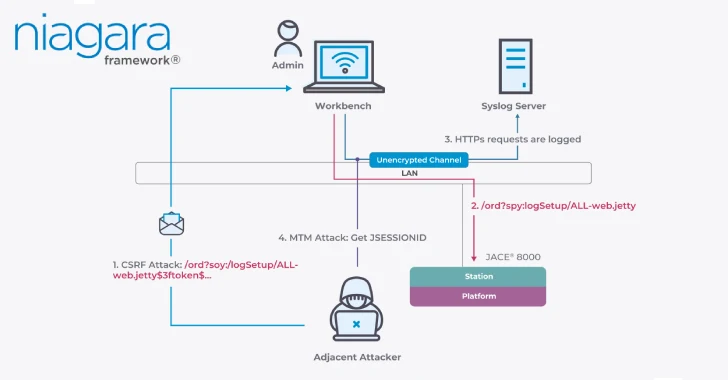
Cybersecurity researchers have discovered over a dozen security vulnerabilities impacting Tridium’s Niagara Framework that could allow an attacker on the…
Jul 25, 2025Ravie LakshmananMalware / Threat Intelligence The threat actor known as Patchwork has been attributed to a new spear-phishing…
Jul 25, 2025Ravie LakshmananCybercrime / Insider Threat The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned…
Jul 25, 2025Ravie LakshmananCyber Espionage / Malware Russian aerospace and defense industries have become the target of a cyber espionage…
Jul 25, 2025The Hacker NewsArtificial Intelligence / Data Privacy A recent analysis of enterprise data suggests that generative AI tools…
Jul 25, 2025Ravie LakshmananMalware / Cloud Security Threat hunters have disclosed two different malware campaigns that have targeted vulnerabilities and…
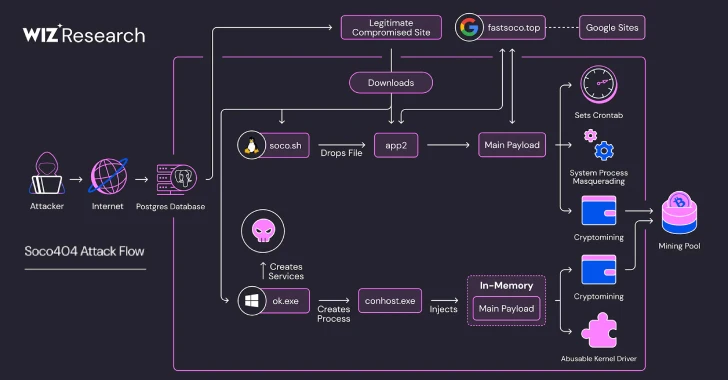
Jul 24, 2025Ravie LakshmananVirtualization / Network Security Virtualization and networking infrastructure have been targeted by a threat actor codenamed Fire…