Category: TheHackerNews
Jul 24, 2025Ravie LakshmananVulnerability / Network Security Mitel has released security updates to address a critical security flaw in MiVoice…
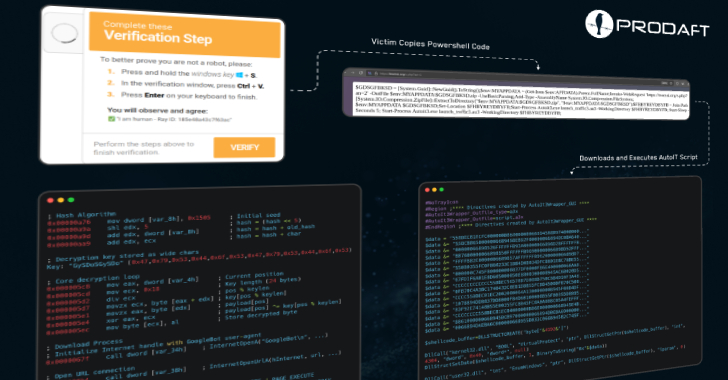
Jul 24, 2025Ravie LakshmananMalware / Cybercrime Cybersecurity researchers have shed light on a new versatile malware loader called CastleLoader that…
Jul 24, 2025Ravie LakshmananNetwork Security / Vulnerability Sophos and SonicWall have alerted users of critical security flaws in Sophos Firewall…
Jul 24, 2025Ravie LakshmananCyber Espionage / Malware The Tibetan community has been targeted by a China-nexus cyber espionage group as…
You wouldn’t run your blue team once a year, so why accept this substandard schedule for your offensive side? Your…
Jul 24, 2025The Hacker News Is Managing Customer Logins and Data Giving You Headaches? You’re Not Alone! Today, we all…
Jul 24, 2025Ravie LakshmananVulnerability / Ransomware Microsoft has revealed that one of the threat actors behind the active exploitation of…
Europol on Monday announced the arrest of the suspected administrator of XSS.is (formerly DaMaGeLaB), a notorious Russian-speaking cybercrime platform. The…
Jul 24, 2025Ravie LakshmananCybersecurity / Web Security Cybersecurity researchers have uncovered a new stealthy backdoor concealed within the “mu-plugins” directory…
Jul 23, 2025Ravie LakshmananMalware / Cryptocurrency The threat actor behind the exploitation of vulnerable Craft Content Management System (CMS) instances…
Jul 23, 2025Ravie LakshmananWindows Security / Cryptocurrency The Windows banking trojan known as Coyote has become the first known malware…
Security experts have been talking about Kerberoasting for over a decade, yet this attack continues to evade typical defense methods….