Category: TheHackerNews
Jul 21, 2025Ravie LakshmananWeb Security / Cryptocurrency A new attack campaign has compromised more than 3,500 websites worldwide with JavaScript…
Jul 21, 2025Ravie LakshmananNetwork Security / Vulnerability Hewlett-Packard Enterprise (HPE) has released security updates to address a critical security flaw…
Microsoft on Sunday released security patches for an actively exploited security flaw in SharePoint and also released details of another…
Jul 20, 2025Ravie LakshmananAI Security / Infostealers The financially motivated threat actor known as EncryptHub (aka LARVA-208 and Water Gamayun)…
Jul 20, 2025Ravie LakshmananDevOps / Threat Intelligence Cybersecurity researchers have alerted to a supply chain attack that has targeted popular…
Jul 20, 2025Ravie LakshmananZero-Day / Vulnerability A critical security vulnerability in Microsoft SharePoint Server has been weaponized as part of…
Jul 20, 2025Ravie LakshmananVulnerability / Threat Intelligence A newly disclosed critical security flaw in CrushFTP has come under active exploitation…
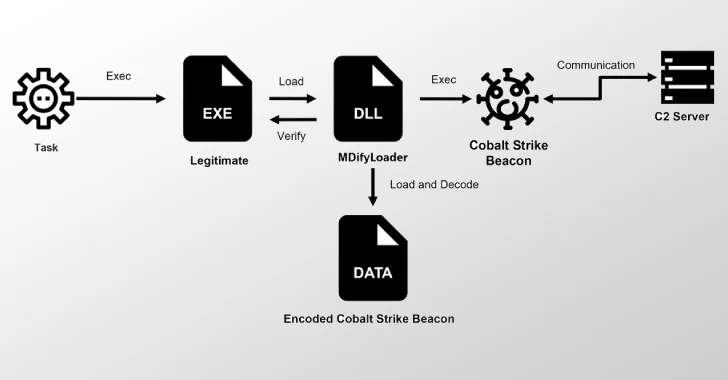
Jul 18, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have disclosed details of a new malware called MDifyLoader that has been…
Jul 18, 2025Ravie LakshmananCyber Espionage / Malware Multiple sectors in China, Hong Kong, and Pakistan have become the target of…
Jul 18, 2025Ravie LakshmananSurveillance / Mobile Security Cybersecurity researchers have shed light on a mobile forensics tool called Massistant that’s…
With IT outages and disruptions escalating, IT teams are shifting their focus beyond simply backing up data to maintaining operations…
Jul 18, 2025Ravie LakshmananCyber Attack / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed details of a…