Category: TheHackerNews
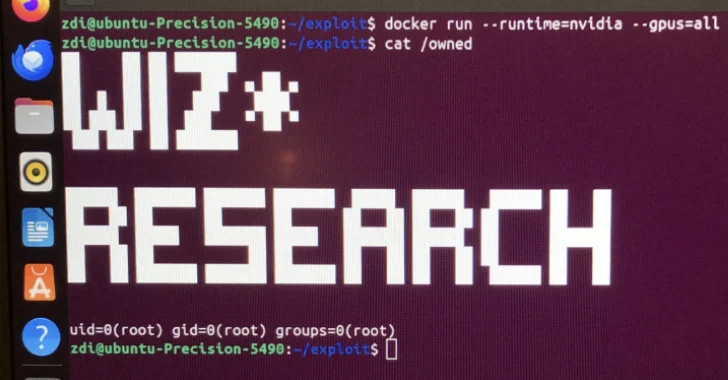
Jul 18, 2025Ravie LakshmananCloud Security / AI Security Cybersecurity researchers have disclosed a critical container escape vulnerability in the NVIDIA…
Jul 18, 2025Ravie LakshmananBotnet / Network Security Google on Thursday revealed it’s pursuing legal action in New York federal court…
Jul 17, 2025Ravie LakshmananMalware / Social Engineering Threat actors are leveraging public GitHub repositories to host malicious payloads and distribute…
Jul 17, 2025Ravie LakshmananCryptocurrency / Vulnerability Cybersecurity researchers have discovered a new campaign that exploits a known security flaw impacting…
The modern-day threat landscape requires enterprise security teams to think and act beyond traditional cybersecurity measures that are purely passive…
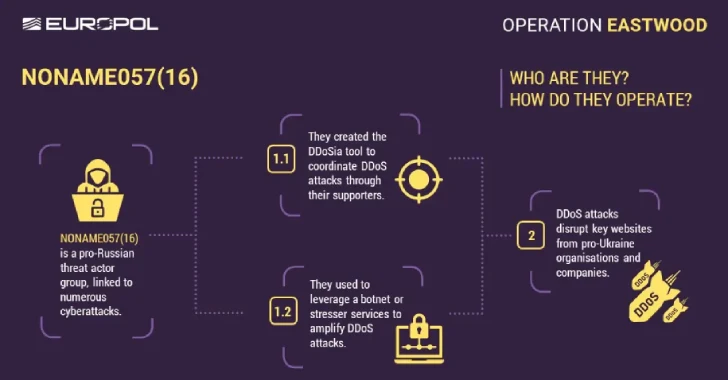
An international operation coordinated by Europol has disrupted the infrastructure of a pro-Russian hacktivist group known as NoName057(16) that has…
The Taiwanese semiconductor industry has become the target of spear-phishing campaigns undertaken by three Chinese state-sponsored threat actors. “Targets of…
Jul 17, 2025Ravie LakshmananVulnerability / Network Security Cisco has disclosed a new maximum-severity security vulnerability impacting Identity Services Engine (ISE)…
Jul 16, 2025Ravie LakshmananThreat Intelligence / Vulnerability Cybersecurity researchers have flagged a new variant of a known malware loader called…
A threat activity cluster has been observed targeting fully-patched end-of-life SonicWall Secure Mobile Access (SMA) 100 series appliances as part…
Jul 16, 2025The Hacker NewsIdentity Management / AI Security The AI gold rush is on. But without identity-first security, every…
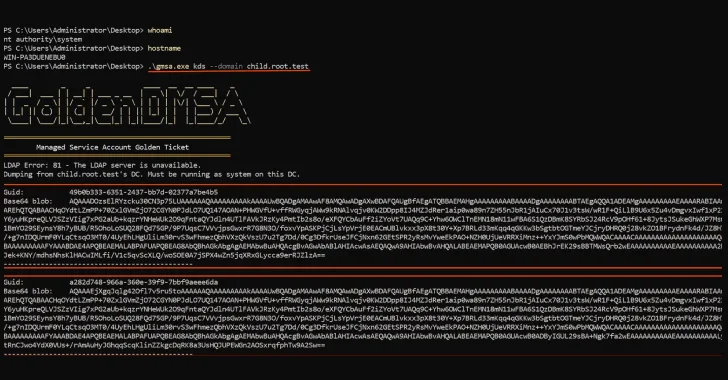
Jul 16, 2025Ravie LakshmananWindows Server / Enterprise Security Cybersecurity researchers have disclosed what they say is a “critical design flaw”…