Category: TheHackerNews
Jul 16, 2025The Hacker NewsAI Security / Fraud Detection Social engineering attacks have entered a new era—and they’re coming fast,…
Jul 16, 2025Ravie LakshmananBrowser Security / Zero-Day Google on Tuesday rolled out fixes for six security issues in its Chrome…
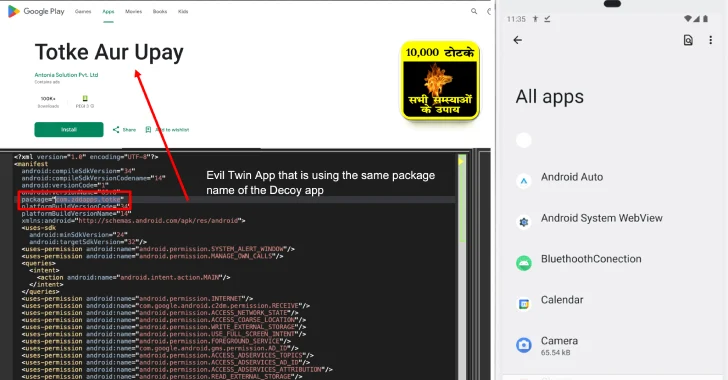
Cybersecurity researchers have discovered a new, sophisticated variant of a known Android malware referred to as Konfety that leverages the…
Cybersecurity researchers have discovered a new, sophisticated variant of a known Android malware referred to as Konfety that leverages the…
Jul 16, 2025Ravie LakshmananAI Security / Vulnerability Google on Tuesday revealed that its large language model (LLM)-assisted vulnerability discovery framework…
Jul 15, 2025Ravie LakshmananBotnet / Network Security Cloudflare on Tuesday said it mitigated 7.3 million distributed denial-of-service (DDoS) attacks in…
Cybersecurity researchers have shed light on a new ransomware-as-a-service (RaaS) operation called GLOBAL GROUP that has targeted a wide range…
Cybersecurity researchers have charted the evolution of a widely used remote access trojan called AsyncRAT, which was first released on…
Jul 15, 2025The Hacker NewsAutomation / Risk Management AI agents promise to automate everything from financial reconciliations to incident response….
Jul 15, 2025Ravie LakshmananCyber Espionage / Threat Intelligence Governmental organizations in Southeast Asia are the target of a new campaign…
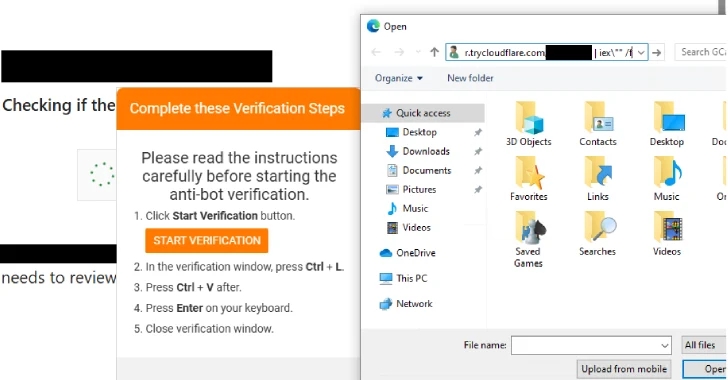
Jul 15, 2025Ravie LakshmananMalware / Web Security The North Korean threat actors linked to the Contagious Interview campaign have been…
Jul 14, 2025Ravie LakshmananMalware / Web Security Threat actors behind the Interlock ransomware group have unleashed a new PHP variant…