Category: TheHackerNews
Jul 14, 2025The Hacker NewsSecrets Management / SaaS Security While phishing and ransomware dominate headlines, another critical risk quietly persists…
Jul 14, 2025Ravie LakshmananCybercrime / Law Enforcement India’s Central Bureau of Investigation (CBI) has announced that it has taken steps…
Jul 14, 2025Ravie LakshmananMobile Security / Vulnerability Cybersecurity researchers have discovered a new hacking technique that exploits weaknesses in the…
Jul 12, 2025Ravie LakshmananAI Security / Vulnerability NVIDIA is urging customers to enable System-level Error Correction Codes (ECC) as a…
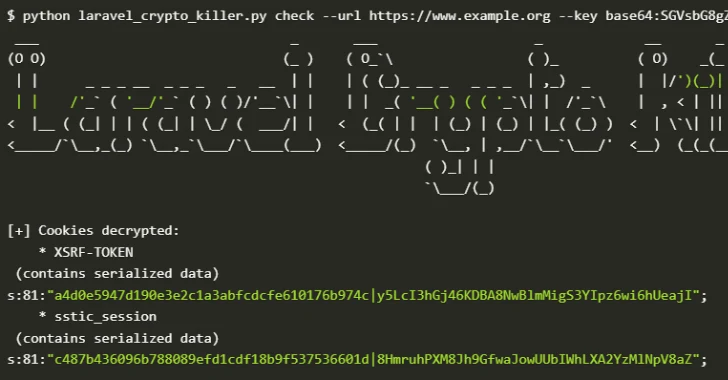
Cybersecurity researchers have discovered a serious security issue that allows leaked Laravel APP_KEYs to be weaponized to gain remote code…
Jul 11, 2025Ravie LakshmananUnited States Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an…
An Iranian-backed ransomware-as-a-service (RaaS) named Pay2Key has resurfaced in the wake of the Israel-Iran-U.S. conflict last month, offering bigger payouts…
Jul 11, 2025Ravie LakshmananCyber Attack / Vulnerability A recently disclosed maximum-severity security flaw impacting the Wing FTP Server has come…
Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could…
Jul 11, 2025Ravie LakshmananCyber Attack / Vulnerability A recently disclosed maximum-severity security flaw impacting the Wing FTP Server has come…
Jul 11, 2025The Hacker NewsData Security / Enterprise Security The 2025 Data Risk Report: Enterprises face potentially serious data loss…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting Citrix NetScaler ADC and…