Category: TheHackerNews
Threat actors are weaponizing exposed Java Debug Wire Protocol (JDWP) interfaces to obtain code execution capabilities and deploy cryptocurrency miners…
Jul 05, 2025Ravie LakshmananNational Security / Privacy Taiwan’s National Security Bureau (NSB) has warned that China-developed applications like RedNote (aka…
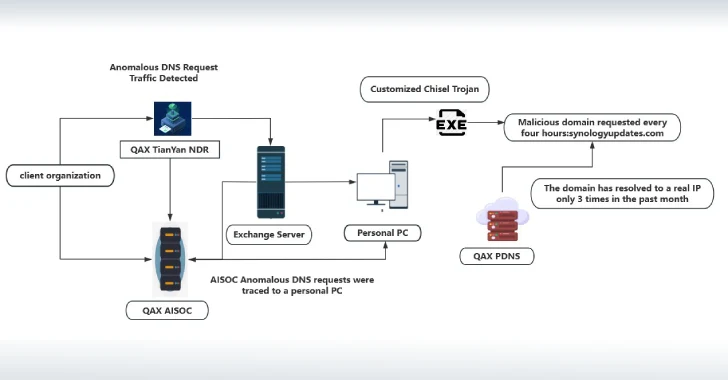
Jul 04, 2025Ravie LakshmananZero-Day / Cyber Espionage Cybersecurity researchers have shed light on a previously undocumented threat actor called NightEagle…
Jul 04, 2025Ravie LakshmananVulnerability / Linux Cybersecurity researchers have disclosed two security flaws in the Sudo command-line utility for Linux…
Jul 04, 2025The Hacker NewsAI Security / Enterprise Security Generative AI is changing how businesses work, learn, and innovate. But…
Jul 04, 2025Ravie LakshmananMobile Security / Privacy Google has been ordered by a court in the U.S. state of California…
A mobile ad fraud operation dubbed IconAds that consisted of 352 Android apps has been disrupted, according to a new…
Jul 03, 2025Ravie LakshmananBrowser Security / Cryptocurrency Cybersecurity researchers have uncovered over 40 malicious browser extensions for Mozilla Firefox that…
Jul 03, 2025Ravie LakshmananThreat Intelligence / Vulnerability The French cybersecurity agency on Tuesday revealed that a number of entities spanning…
If you’re evaluating AI-powered SOC platforms, you’ve likely seen bold claims: faster triage, smarter remediation, and less noise. But under…
Jul 03, 2025Ravie LakshmananVulnerability / Network Security Cisco has released security updates to address a maximum-severity security flaw in Unified…
Threat actors with ties to North Korea have been observed targeting Web3 and cryptocurrency-related businesses with malware written in the…