Category: TheHackerNews
Cybersecurity researchers are calling attention to phishing campaigns that impersonate popular brands and trick targets into calling phone numbers operated…
Jul 02, 2025The Hacker NewsNetwork Security / Threat Detection With nearly 80% of cyber threats now mimicking legitimate user behavior,…
Jul 02, 2025Ravie LakshmananCybercrime / Dark Web The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has…
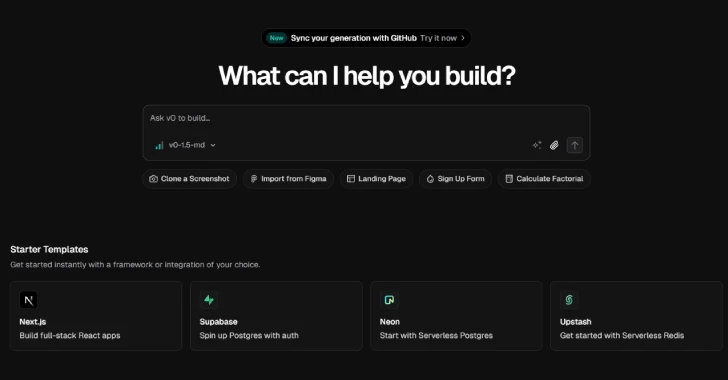
Jul 02, 2025Ravie LakshmananAI Security / Phishing Unknown threat actors have been observed weaponizing v0, a generative artificial intelligence (AI)…
Cybersecurity researchers have discovered a critical security vulnerability in artificial intelligence (AI) company Anthropic’s Model Context Protocol (MCP) Inspector project…
Cybersecurity researchers have flagged the tactical similarities between the threat actors behind the RomCom RAT and a cluster that has…
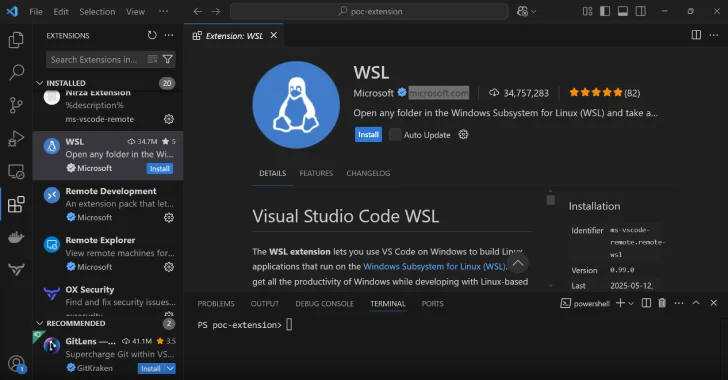
Jul 01, 2025Ravie LakshmananDeveloper Security / Software Development A new study of integrated development environments (IDEs) like Microsoft Visual Studio…
Despite years of investment in Zero Trust, SSE, and endpoint protection, many enterprises are still leaving one critical layer exposed:…
Jul 01, 2025Ravie LakshmananVulnerability / Browser Security Google has released security updates to address a vulnerability in its Chrome browser…
The U.S. Department of Justice (DoJ) on Monday announced sweeping actions targeting the North Korean information technology (IT) worker scheme,…
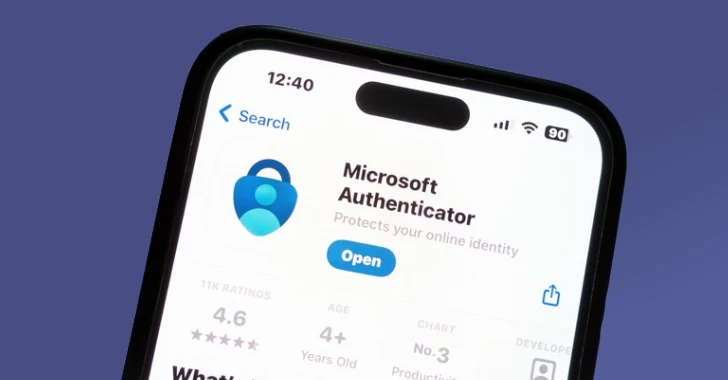
Jul 01, 2025Ravie LakshmananMobile Security / Privacy Microsoft has said that it’s ending support for passwords in its Authenticator app…
Jun 30, 2025Ravie LakshmananCyber Attack / Critical Infrastructure U.S. cybersecurity and intelligence agencies have issued a joint advisory warning of…