Category: TheHackerNews
Jun 26, 2025Ravie LakshmananOpen Source / Vulnerability Cybersecurity researchers have disclosed a critical vulnerability in the Open VSX Registry (“open-vsx[.]org”)…
Jun 26, 2025Ravie LakshmananCyber Attack / Malware Analysis The ClickFix social engineering tactic as an initial access vector using fake…
Jun 26, 2025Ravie LakshmananVulnerability, Network Security Cisco has released updates to address two maximum-severity security flaws in Identity Services Engine…
SaaS Adoption is Skyrocketing, Resilience Hasn’t Kept Pace SaaS platforms have revolutionized how businesses operate. They simplify collaboration, accelerate deployment,…
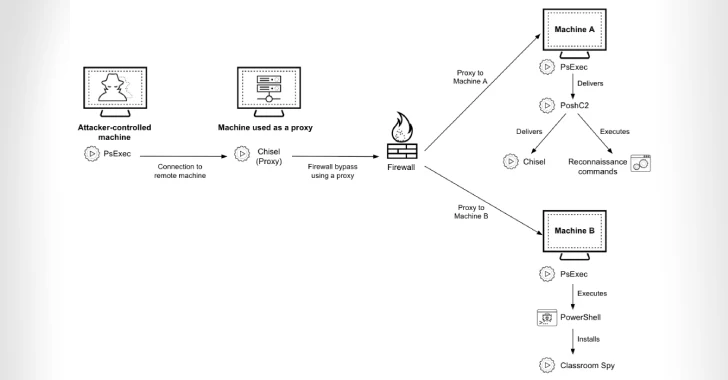
Jun 26, 2025Ravie LakshmananCyber Espionage / Malware An Iranian state-sponsored hacking group associated with the Islamic Revolutionary Guard Corps (IRGC)…
Jun 26, 2025Ravie LakshmananThreat Intelligence / Ransomware Cybersecurity researchers are calling attention to a series of cyber attacks targeting financial…
Jun 26, 2025Ravie LakshmananVulnerability / Firmware Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added three security…
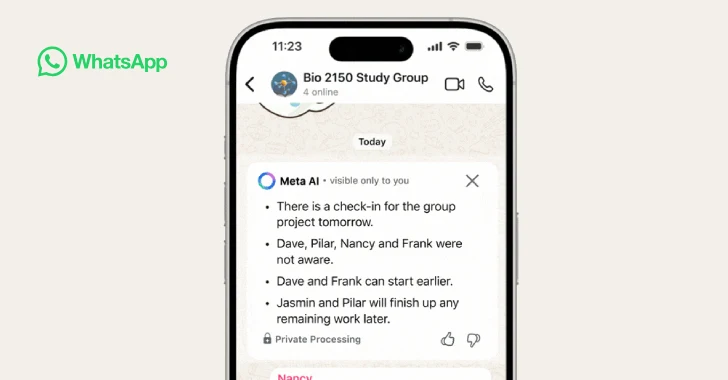
Jun 26, 2025Ravie LakshmananArtificial Intelligence / Data Protection Popular messaging platform WhatsApp has added a new artificial intelligence (AI)-powered feature…
Jun 25, 2025Ravie LakshmananSaaS Security / Vulnerability New research has uncovered continued risk from a known security weakness in Microsoft’s…
Jun 25, 2025Ravie LakshmananVulnerability / Network Security Citrix has released security updates to address a critical flaw affecting NetScaler ADC…
Jun 25, 2025Ravie LakshmananData Privacy / Vulnerability Cybersecurity researchers have detailed two now-patched security flaws in SAP Graphical User Interface…
If you invite guest users into your Entra ID tenant, you may be opening yourself up to a surprising risk….