Category: TheHackerNews
Jun 24, 2025Ravie LakshmananCyber Espionage / Chinese Hackers The Canadian Centre for Cyber Security and the U.S. Federal Bureau of…
Jun 23, 2025Ravie LakshmananHacktivism / Cyber Warfare The United States government has warned of cyber attacks mounted by pro-Iranian groups…
Jun 23, 2025Ravie LakshmananLLM Security / AI Security Cybersecurity researchers are calling attention to a new jailbreaking method called Echo…
Jun 23, 2025Ravie LakshmananCyber Espionage / Vulnerability Cybersecurity researchers have uncovered a Go-based malware called XDigo that has been used…
It sure is a hard time to be a SOC analyst. Every day, they are expected to solve high-consequence problems…
Google has revealed the various safety measures that are being incorporated into its generative artificial intelligence (AI) systems to mitigate…
Jun 21, 2025Ravie LakshmananCyber Attack / Critical Infrastructure The April 2025 cyber attacks targeting U.K. retailers Marks & Spencer and…
The threat actors behind the Qilin ransomware-as-a-service (RaaS) scheme are now offering legal counsel for affiliates to put more pressure…
Jun 20, 2025Ravie LakshmananCyber Warfare / Hacktivism Iran’s state-owned TV broadcaster was hacked Wednesday night to interrupt regular programming and…
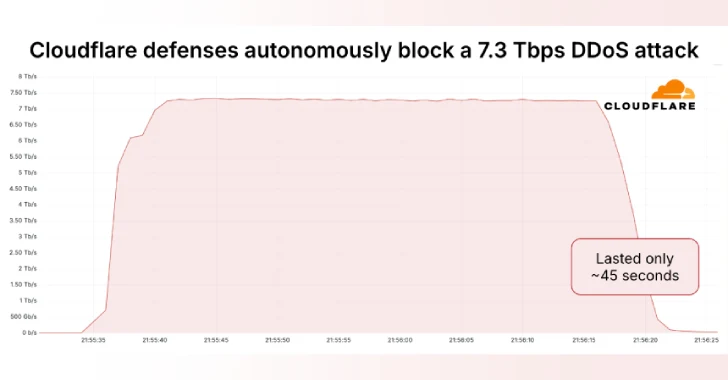
Cloudflare on Thursday said it autonomously blocked the largest ever distributed denial-of-service (DDoS) attack ever recorded, which hit a peak…
Hackers never sleep, so why should enterprise defenses? Threat actors prefer to target businesses during off-hours. That’s when they can…
Cybersecurity researchers have uncovered a new campaign in which the threat actors have published more than 67 GitHub repositories that…