Category: TheHackerNews
Generative AI is not arriving with a bang, it’s slowly creeping into the software that companies already use on a…
A high-severity security flaw has been disclosed in ServiceNow’s platform that, if successfully exploited, could result in data exposure and…
Jul 09, 2025Ravie LakshmananCyber Threat / Malware The Initial Access Broker (IAB) known as Gold Melody has been attributed to…
Jul 09, 2025Ravie LakshmananMalware / Cyber Espionage A threat actor with suspected ties to India has been observed targeting a…
Jul 09, 2025The Hacker NewsSecurity Operations / Automation Run by the team at workflow orchestration and AI platform Tines, the…
Jul 09, 2025Ravie LakshmananMalware / Cyber Crime The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) on…
Jul 09, 2025Ravie LakshmananCyber Espionage / Threat Intelligence A Chinese national has been arrested in Milan, Italy, for his alleged…
For the first time in 2025, Microsoft’s Patch Tuesday updates did not bundle fixes for exploited security vulnerabilities, but acknowledged…
Jul 08, 2025Ravie LakshmananMalware / Cybercrime In yet another instance of threat actors repurposing legitimate tools for malicious purposes, it…
Jul 08, 2025Ravie LakshmananMalware / Mobile Security Cybersecurity researchers have discovered an Android banking malware campaign that has leveraged a…
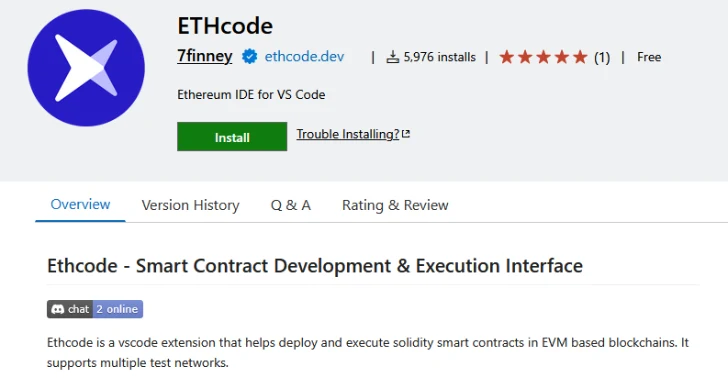
Cybersecurity researchers have flagged a supply chain attack targeting a Microsoft Visual Studio Code (VS Code) extension called Ethcode that…
A newly released report by cybersecurity firm CTM360 reveals a large-scale scam operation utilizing fake news websites—known as Baiting News…