Category: TheHackerNews
Jun 12, 2025The Hacker NewsArtificial Intelligence / SaaS Security AI is changing everything — from how we code, to how…
Human identities management and control is pretty well done with its set of dedicated tools, frameworks, and best practices. This…
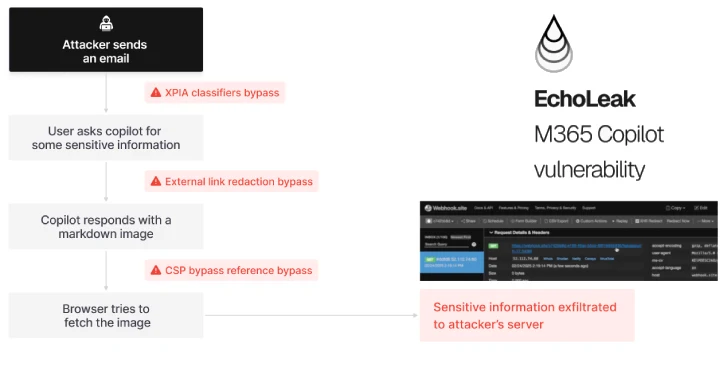
A novel attack technique named EchoLeak has been characterized as a “zero-click” artificial intelligence (AI) vulnerability that allows bad actors…
Jun 12, 2025Ravie LakshmananVulnerability / Software Security ConnectWise has disclosed that it’s planning to rotate the digital code signing certificates…
Jun 12, 2025Ravie LakshmananEnterprise Security / Active Directory Cybersecurity researchers have uncovered a new account takeover (ATO) campaign that leverages…
Jun 11, 2025Ravie LakshmananRansomware / Cybercrime Former members tied to the Black Basta ransomware operation have been observed sticking to…
Jun 11, 2025Ravie LakshmananNetwork Security / Threat Intelligence Threat intelligence firm GreyNoise has warned of a “coordinated brute-force activity” targeting…
In today’s cybersecurity landscape, much of the focus is placed on firewalls, antivirus software, and endpoint detection. While these tools…
Jun 11, 2025Ravie LakshmananCybercrime / Malware INTERPOL on Wednesday announced the dismantling of more than 20,000 malicious IP addresses or…
In today’s security landscape, budgets are tight, attack surfaces are sprawling, and new threats emerge daily. Maintaining a strong security…
Jun 11, 2025Ravie LakshmananIoT Security / Vulnerability Two security vulnerabilities have been disclosed in SinoTrack GPS devices that could be…
Microsoft has released patches to fix 67 security flaws, including one zero-day bug in Web Distributed Authoring and Versioning (WEBDAV)…