Category: TheHackerNews
Cybersecurity researchers have flagged a supply chain attack targeting over a dozen packages associated with GlueStack to deliver malware. The…
Jun 08, 2025Ravie LakshmananMalware / Browser Security Cybersecurity researchers have shed light on a new campaign targeting Brazilian users since…
Cybersecurity researchers are alerting to a new malware campaign that employs the ClickFix social engineering tactic to trick users into…
Jun 06, 2025The Hacker NewsCybercrime / Financial Fraud India’s Central Bureau of Investigation (CBI) has revealed that it has arrested…
Jun 06, 2025The Hacker NewsArtificial Intelligence / Zero Trust When generative AI tools became widely available in late 2022, it…
Jun 06, 2025The Hacker NewsCyber Resilience / Penetration Testing Cybersecurity involves both playing the good guy and the bad guy….
A critical infrastructure entity within Ukraine was targeted by a previously unseen data wiper malware named PathWiper, according to new…
Jun 05, 2025Ravie LakshmananBrowser Security / Online Safety Cybersecurity researchers have flagged several popular Google Chrome extensions that have been…
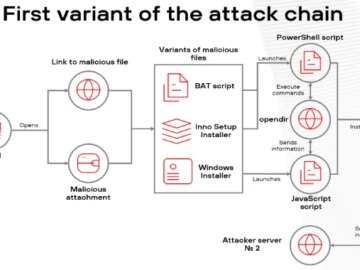
Jun 05, 2025Ravie LakshmananThreat Intelligence / Network Security The threat actor known as Bitter has been assessed to be a…
An Iran-aligned hacking group has been attributed to a new set of cyber attacks targeting Kurdish and Iraqi government officials…
Security teams face growing demands with more tools, more data, and higher expectations than ever. Boards approve large security budgets,…
Jun 05, 2025Ravie LakshmananDark Web / Law Enforcement The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of…