Category: TheHackerNews
Jun 03, 2025Ravie LakshmananBrowser Security / Vulnerability Google on Monday released out-of-band fixes to address three security issues in its…
Jun 02, 2025Ravie LakshmananMobile Security / Vulnerability Three security vulnerabilities have been disclosed in preloaded Android applications on smartphones from…
Cybersecurity researchers have discovered a new cryptojacking campaign that’s targeting publicly accessible DevOps web servers such as those associated with…
Jun 02, 2025Ravie LakshmananSpyware / Vulnerability Qualcomm has shipped security updates to address three zero-day vulnerabilities that it said have…
The evolution of cyber threats has forced organizations across all industries to rethink their security strategies. As attackers become more…
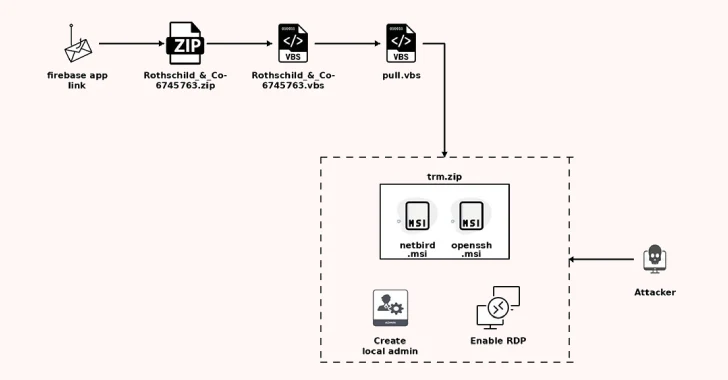
Cybersecurity researchers have warned of a new spear-phishing campaign that uses a legitimate remote access tool called Netbird to target…
May 31, 2025Ravie LakshmananMalware / Cyber Crime A multinational law enforcement operation has resulted in the takedown of an online…
May 31, 2025Ravie LakshmananVulnerability / Linux Two information disclosure flaws have been identified in apport and systemd-coredump, the core dump…
Meta on Thursday revealed that it disrupted three covert influence operations originating from Iran, China, and Romania during the first…
May 30, 2025Ravie LakshmananVulnerability / Data Breach ConnectWise, the developer of remote access and support software ScreenConnect, has disclosed that…
May 30, 2025Ravie LakshmananCryptocurrency / Cybercrime The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) has levied sanctions…
Breaking Out of the Security Mosh Pit When Jason Elrod, CISO of MultiCare Health System, describes legacy healthcare IT environments,…