Category: TheHackerNews
May 20, 2025Ravie LakshmananCredential Theft / Browser Security An unknown threat actor has been attributed to creating several malicious Chrome…
Cybersecurity researchers have discovered risky default identity and access management (IAM) roles impacting Amazon Web Services that could open the…
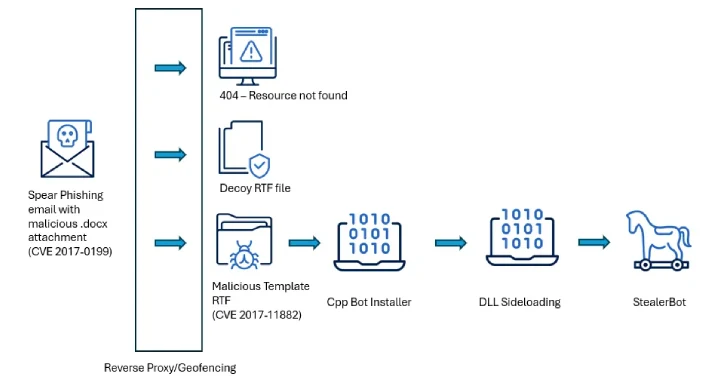
May 20, 2025Ravie LakshmananMalware / Cyber Espionage High-level government institutions in Sri Lanka, Bangladesh, and Pakistan have emerged as the…
May 20, 2025The Hacker NewsPenetration Testing / Risk Management In the newly released 2025 State of Pentesting Report, Pentera surveyed…
May 20, 2025Ravie LakshmananMalware / Cyber Espionage Threat hunters have exposed the tactics of a China-aligned threat actor called UnsolicitedBooker…
May 20, 2025Ravie LakshmananLinux / Cryptojacking Cybersecurity researchers are calling attention to a new Linux cryptojacking campaign that’s targeting publicly…
Cybersecurity researchers have uncovered malicious packages uploaded to the Python Package Index (PyPI) repository that act as checker tools to…
May 19, 2025Ravie LakshmananMalware / Supply Chain Attack The official site for RVTools has been hacked to serve a compromised…
May 19, 2025Ravie LakshmananRansomware / Malware Several ransomware actors are using a malware called Skitnet as part of their post-exploitation…
May 19, 2025Ravie LakshmananBrowser Security / Vulnerability Mozilla has released security updates to address two critical security flaws in its…
Continuous Threat Exposure Management (CTEM) has moved from concept to cornerstone, solidifying its role as a strategic enabler for CISOs….
May 16, 2025Ravie LakshmananUnited States Cybersecurity researchers are calling attention to a new botnet malware called HTTPBot that has been…