Category: welivesecurity
Your iPhone isn’t necessarily as invulnerable to security threats as you may think. Here are the key dangers to watch…
Look out for AI-generated ‘TikDocs’ who exploit the public’s trust in the medical profession to drive sales of sketchy supplements…
The form and quiz-building tool is a popular vector for social engineering and malware. Here’s how to stay safe. 23…
What practical AI attacks exist today? “More than zero” is the answer – and they’re getting better. 22 Apr 2025…
Cybercriminals lure content creators with promises of cutting-edge AI wizardry, only to attempt to steal their data or hijack their…
Here’s what to know about malware that raids email accounts, web browsers, crypto wallets, and more – all in a…
Academic institutions have a unique set of characteristics that makes them attractive to bad actors. What’s the right antidote to…
The pioneering multi-media artist reveals the creative process behind her stage show called ARK, which challenges audiences to reflect on…
Ransomware payments trending down, the cyber-resilience gap facing SMBs, and APT groups embracing generative AI – it’s a wrap on…
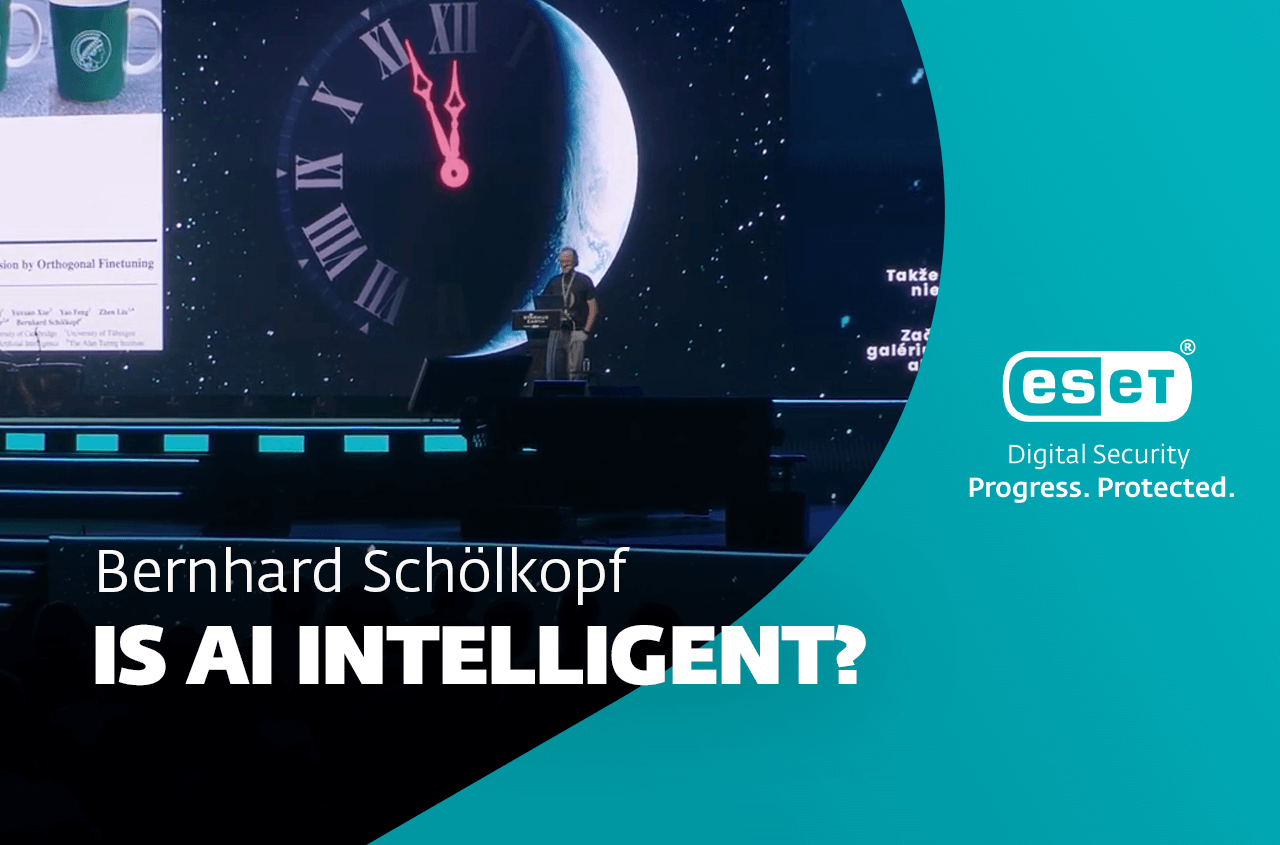
With AI’s pattern recognition capabilities well-established, Mr. Schölkopf’s talk shifts the focus to a pressing question: what will be the…
Big shifts in the infostealer scene, novel attack vector against iOS and Android, and a massive surge in investment scams…
Take a moment to think beyond our current capabilities and consider what might come next in the grand story of…