Category: welivesecurity
By taking time to understand and communicate the impact of undesirable online behavior, you can teach your kids an invaluable…
Malicious use of AI is reshaping the fraud landscape, creating major new risks for businesses 10 Mar 2025 • ,…
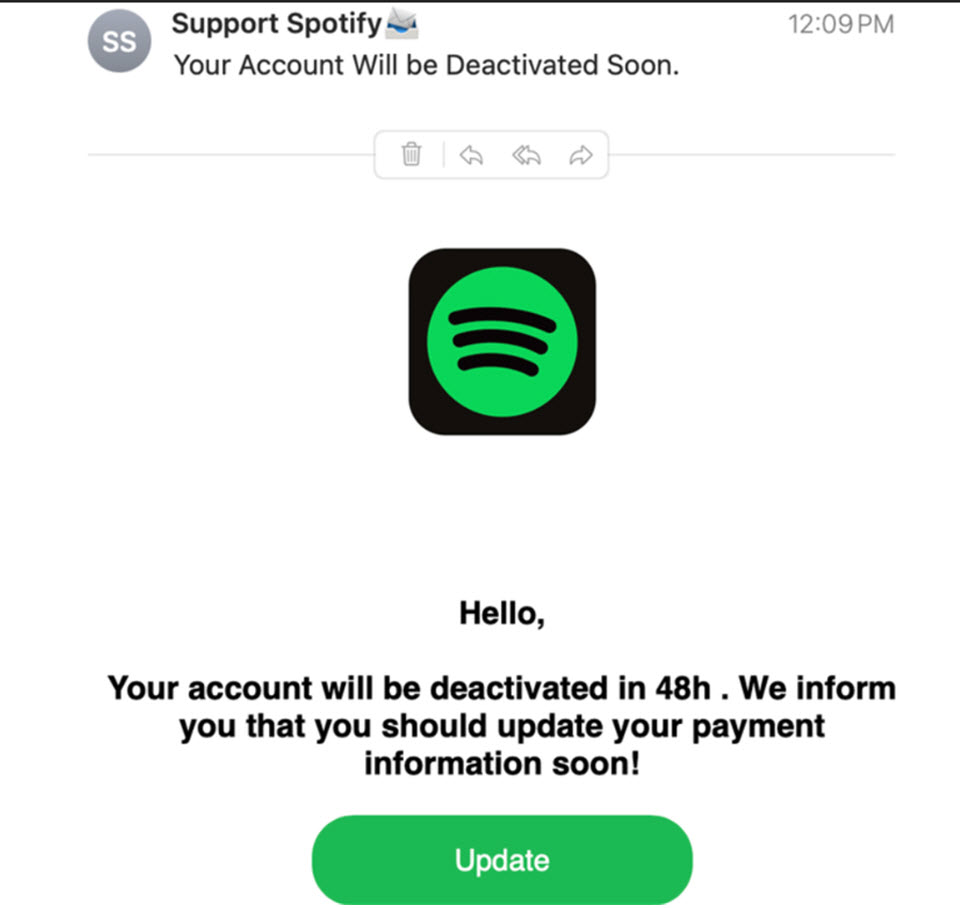
Spotify boasts almost 700 million active users, including 265 million premium subscribers. As the world’s leading music streaming service, it’s…
While relatively rare, real-world incidents impacting operational technology highlight that organizations in critical infrastructure can’t afford to dismiss the OT…
Here’s what’s been hot on the AI scene over the past 12 months, how it’s changing the face of warfare,…
The group’s Operation AkaiRyū begins with targeted spearphishing emails that use the upcoming World Expo 2025 in Osaka, Japan, as…
Once thought to be dormant, the China-aligned group has also been observed using the privately-sold ShadowPad backdoor for the first…
ESET researchers also examine the growing threat posed by tools that ransomware affiliates deploy in an attempt to disrupt EDR…
Security awareness training doesn’t have to be a snoozefest – games and stories can help instill ‘sticky’ habits that will…
Here’s how to avoid being hit by fraudulent websites that scammers can catapult directly to the top of your search…
Business Security Ransomware Your company’s ability to tackle the ransomware threat head-on can ultimately be a competitive advantage 31 Mar…
From an exploited vulnerability in a third-party ChatGPT tool to a bizarre twist on ransomware demands, it’s a wrap on…