Category: welivesecurity
The attacks used spearphishing campaigns to target financial, manufacturing, defense, and logistics companies in Europe and Canada, ESET research finds…
Is your phone suddenly flooded with aggressive ads, slowing down performance or leading to unusual app behavior? Here’s what to…
A sky-high premium may not always reflect your company’s security posture 08 Aug 2025 • , 3 min. read When…
Success in cybersecurity is when nothing happens, plus other standout themes from two of the event’s keynotes 07 Aug 2025…
Who’s to blame when the AI tool managing a company’s compliance status gets it wrong? 07 Aug 2025 • ,…
Threat actors are embracing ClickFix, ransomware gangs are turning on each other – toppling even the leaders – and law…
Restricting end-to-end encryption on a single-country basis would not only be absurdly difficult to enforce, but it would also fail…
Here’s what you need to know about the inner workings of modern spyware and how to stay away from apps…
Here’s a look at cybersecurity stories that moved the needle, raised the alarm, or offered vital lessons in July 2025…
Not all browser add-ons are handy helpers – some may contain far more than you have bargained for 29 Jul…
The ToolShell bugs are being exploited by cybercriminals and APT groups alike, with the US on the receiving end of…
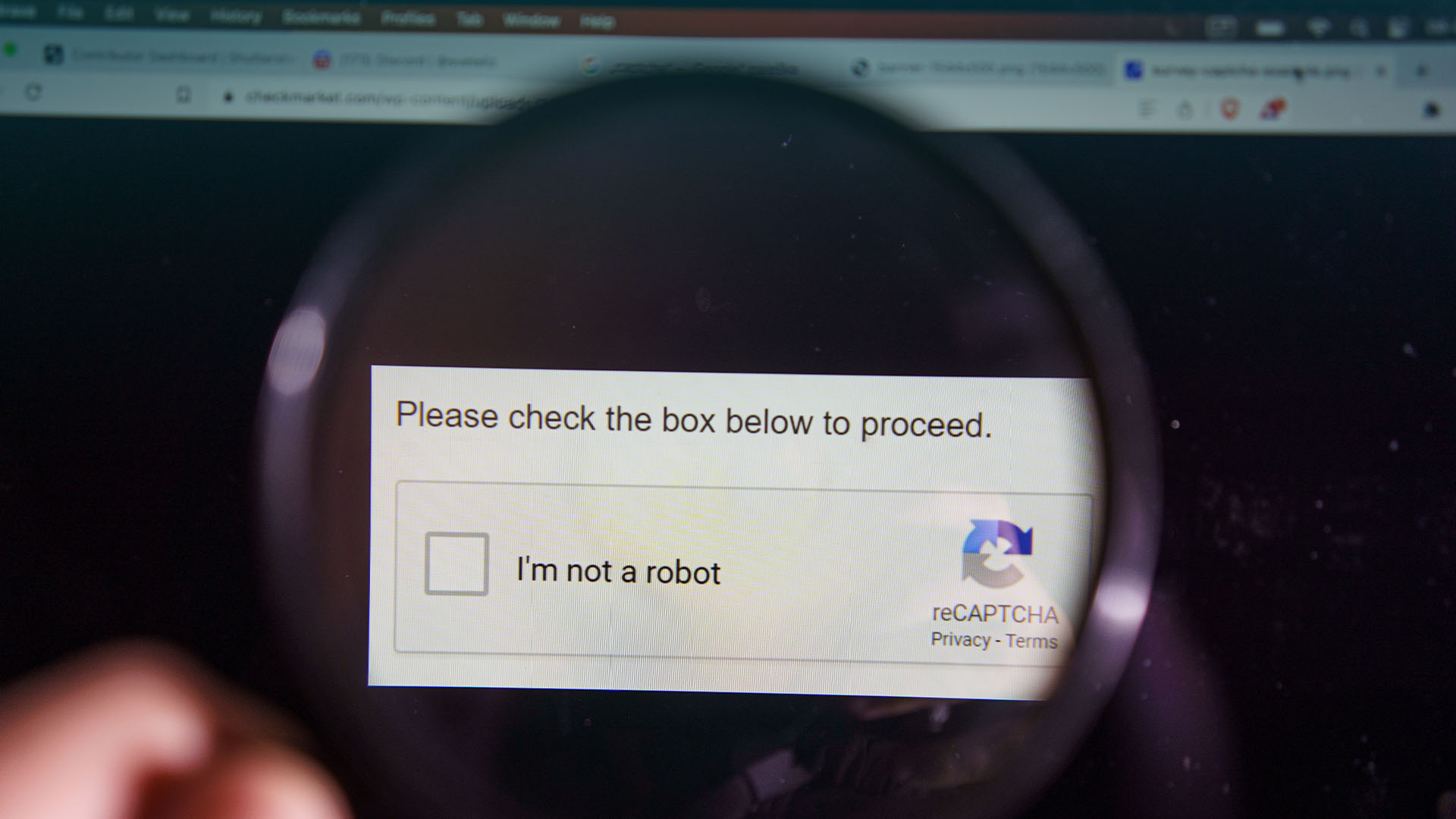
Before rushing to prove that you’re not a robot, be wary of deceptive human verification pages as an increasingly popular…