Adversaries have once again demonstrated that operational hours are irrelevant when mounting sophisticated cyberattacks.
eSentire’s TRU team first observed suspicious activity within a financial services customer’s environment when legitimate CiscoVPN logins coincided with anomalous WMI calls to multiple endpoints.
Investigation revealed that an Active Directory account named “serviceaccount” had been abused alongside the VPN access, granting the attackers broad execution privileges.
In late September 2025, eSentire’s Threat Response Unit (TRU) identified a novel Rust-based backdoor dubbed “ChaosBot” that exploited compromised CiscoVPN credentials and an over-privileged Active Directory account to move laterally, execute remote commands and maintain persistence via Discord-powered command and control.
The payload, msedge_elf.dll, was side-loaded through Microsoft Edge identity_helper.exe from C:UsersPublicLibraries, allowing ChaosBot to deploy undetected.
Initial reconnaissance commands retrieved system information, and a fast reverse proxy (frp) executable was downloaded to establish an inbound tunnel.

Simultaneously, operators tested a VS Code Tunnel backdoor, although that effort faltered due to interactive authentication prompts that the script could not bypass.
Anatomy of the Attack
ChaosBot’s attack chain begins with credential theft—either via brute forcing CiscoVPN logins or through phishing campaigns delivering malicious Windows Shortcut (.lnk) files masquerading as State Bank of Vietnam correspondence.
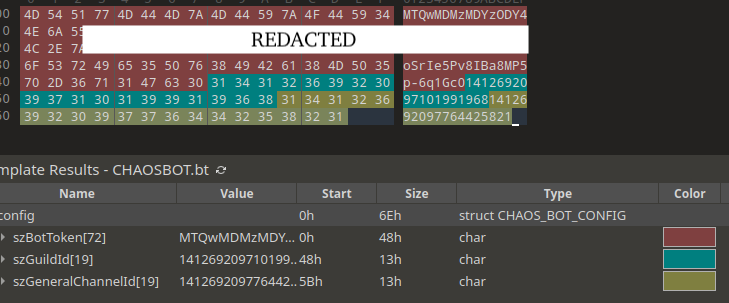
ChaosBot is written in Rust and uses either the reqwest or serenity library for interactions with the Discord API depending on the variant.

Once the victim triggers the shortcut, a PowerShell command fetches and runs ChaosBot, while a decoy PDF opens to dupe the user.
The malware connects to Discord using a bot token embedded in its configuration, validates the token via a GET request to the Discord API, and creates a new channel named after the victim’s hostname.
Subsequent GET requests poll that channel for commands, which ChaosBot executes locally by spawning PowerShell processes. Standardized command lines include UTF-8 output encoding to preserve character integrity.
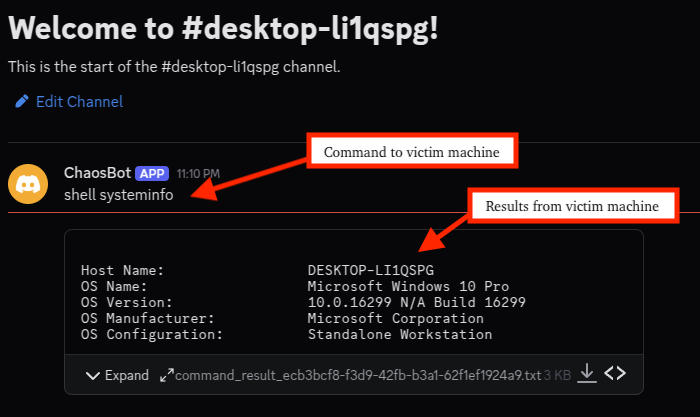
Threat actor’s perspective and highlights how the victim machine’s system information was uploaded to the channel shortly after the threat actor sent the shell command.

Supported commands allow execution of arbitrary shell commands, file download and upload, screenshot capture, and reverse proxy setup.
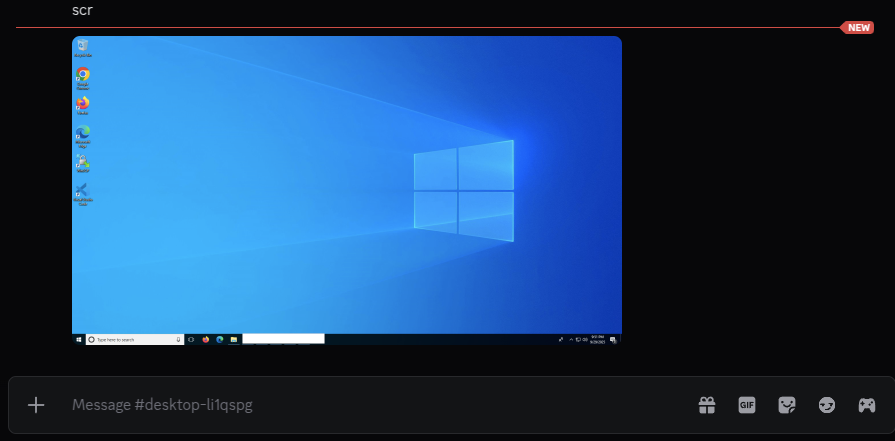
For example, “shell systeminfo” collects and returns system details to the channel, while “scr” captures the desktop and posts a PNG file.
Evasion techniques include patching ntdll!EtwEventWrite to disable Event Tracing for Windows telemetry and checking MAC addresses against known VMware and VirtualBox prefixes to avoid running in virtual machines.
Operators maintain persistence by downloading frp and configuring node.exe with encrypted, compressed tunnels pointing to an AWS Hong Kong server.
Attempts to install a VS Code Tunnel service demonstrated the adversaries’ experimentation with multifaceted backdoors. Analysis of 12 samples confirmed two Discord user accounts—chaos_00019 and lovebb0024—behind the C2 infrastructure, with metadata indicating account creation in mid-2024.
Recommendations and Response
Upon confirmation of the breach, eSentire’s SOC analysts isolated affected hosts and collaborated with the customer to eradicate the threat.
Key lessons include the danger of over-privileged service accounts and the ease with which stolen VPN credentials enable rapid network compromise.
Organizations should enforce least privilege for remote access accounts, mandate multi-factor authentication on all VPN and domain logins, and enforce strong, unpredictable password policies.
This functionality serves as a reconnaissance tool for the malware operators, enabling them to quickly assess whether the infected system is a sandbox or a legitimate target.

Naming conventions for service accounts should avoid common terms like “serviceaccount” to thwart automated attacks.
Beyond credential hygiene, maintaining current security patches, enabling detailed logging of authentication events, and actively monitoring for anomalous remote execution activity are critical.
At a minimum, deploying a Next-Gen Antivirus or Endpoint Detection and Response solution can detect memory patching and abnormal PowerShell behavior.
For comprehensive protection, partnering with a 24/7 Managed Detection and Response provider ensures continuous threat hunting, rapid containment and proactive threat intelligence fed by units like eSentire’s TRU.
By adopting these measures, organizations can minimize the impact of sophisticated backdoors such as ChaosBot and stay one step ahead of adversaries.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
